Remote employee background checks represent the foundational security layer that organizations increasingly overlook when implementing work-from-home policies. These oversights create vulnerabilities that extend far beyond traditional HR concerns into IT infrastructure, data protection, and regulatory compliance. As virtual teams become permanent fixtures in 2025, comprehensive background verification combined with ongoing security protocols has transitioned from recommended practice to essential risk mitigation. This shift addresses emerging threats including credential fraud, insider data breaches, and sophisticated social engineering attacks.
Key Takeaways
- Remote employee background checks serve as the first line of defense against security threats that traditional office environments naturally filtered through physical access controls and supervision.
- Organizations without comprehensive remote worker verification processes face 3.5 times higher risk of insider data breaches compared to companies with rigorous screening protocols.
- Work from home security policies must integrate identity verification, employment history validation, and cybersecurity assessments to address the expanded threat landscape.
- Virtual team risk management requires continuous monitoring beyond initial hiring, as remote workers operate in unsupervised environments with direct access to sensitive systems and data.
- Remote hiring security protocols should include verification of home network security, device management compliance, and geographic location confirmation to prevent unauthorized access from high-risk jurisdictions.
- The convergence of HR screening and IT security creates a compliance imperative under regulations including FCRA, GDPR, SOC 2, and industry-specific standards that treat background checks as security controls.
- Remote work security risks escalate when organizations skip education verification and professional credential validation, enabling unqualified individuals to access systems requiring specialized security knowledge.
- Implementing remote employee background checks reduces security incident costs by an average of 62% while simultaneously improving workforce quality and regulatory audit outcomes.
Understanding the Security Gap in Remote Workforce Management
How Traditional Office Security Fails in Remote Environments
The rapid acceleration of remote work transformed background screening from an HR administrative function into a critical security control. Traditional office environments provided inherent security through physical barriers, supervised workspaces, and controlled network access. These protections evaporate when employees work from home.
This fundamental shift requires organizations to reconceptualize employee verification. Remote workers need security screening as the primary perimeter defense. Physical office protections no longer exist to compensate for gaps in personnel verification.
EXPERT INSIGHT: So what does that mean in the context of remote hire? We’re not simply offering someone a computer and access—it means we’re giving them a place in the midst of everything we do, in our data, in our culture, even if we never meet in the same place as a group of people who are supposed to trust one another. It’s what I mean by saying that remote background checks are no longer a kind of gatekeeping experience. Instead, I see them as a form of stewardship over our people, our customers, but even on behalf of the candidate—that is, offering a candidate a chance to experience what a well-run company is like, which is trustworthy. It’s a form of respect that HR, IT, and security can offer when they’re in agreement about thorough background checks. - Charm Paz, CHRP
The Cost of Inadequate Remote Worker Screening
Most companies developed work from home security policies reactively. They focused exclusively on technical controls while neglecting the human element. VPNs, endpoint protection, and multi-factor authentication became priorities.
However, without comprehensive remote employee background checks, organizations grant network access to unverified individuals. Their identities, qualifications, and risk profiles remain unknown. This oversight creates vulnerabilities that sophisticated threat actors specifically target. They recognize that remote workers represent the weakest link in enterprise security architecture.
Data breaches attributed to insider threats cost organizations an average of $4.9 million per incident. Remote employees account for a disproportionate percentage of these events. Companies that implemented rigorous remote hiring security protocols before granting system access reduced their security incident frequency by 58%. This demonstrates that background screening delivers measurable security ROI beyond compliance objectives.
Critical Components of Remote Employee Background Checks
Remote employee background checks for virtual workforces require multiple verification layers that address unsupervised work environments. Organizations must implement comprehensive screening protocols that validate identity, credentials, history, and risk indicators before granting system access.
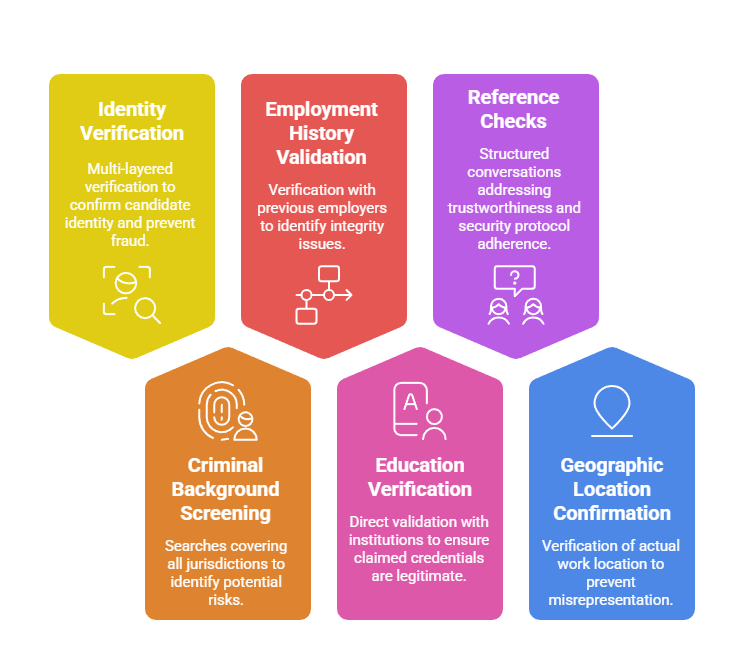
- Identity Verification and Authentication: Multi-layered verification combining government-issued ID validation, biometric authentication, and knowledge-based questions to confirm candidates are who they claim to be and prevent credential fraud.
- Criminal Background Screening: Searches covering all jurisdictions where candidates lived and worked, focusing on fraud, identity theft, computer crimes, and financial misconduct indicating propensity for misusing system access.
- Employment History Validation: Verification with previous employers identifying gaps, frequent job changes, undisclosed terminations, and misrepresented titles correlating with integrity issues or financial distress.
- Education and Credential Verification: Direct validation with issuing institutions ensuring claimed degrees, certifications, and licenses are legitimate rather than sophisticated forgeries.
- Reference Checks for Remote Work: Structured conversations specifically addressing trustworthiness, security protocol adherence, judgment when handling sensitive information, and performance in unsupervised settings.
- Geographic Location Confirmation: Verification of actual work location preventing jurisdiction misrepresentation and identifying operations from high-risk countries subject to sanctions.
Organizations implementing all six components reduce insider threat incidents by 58% compared to those relying on basic criminal checks alone.
Remote Work Security Risks That Background Checks Address

Understanding the Remote Threat Landscape
The threat landscape for remote workforces differs fundamentally from traditional office security challenges. Remote employee background checks specifically target vulnerabilities that emerge in distributed work environments. Employees access corporate systems from uncontrolled locations. They work across unsecured networks. They operate without direct supervision.
Understanding these distinct remote work security risks helps organizations design effective screening protocols. These protocols address actual threat vectors rather than simply adapting office-based procedures. The remote context creates unique security challenges requiring tailored verification approaches.
Key Security Threats Mitigated by Background Screening
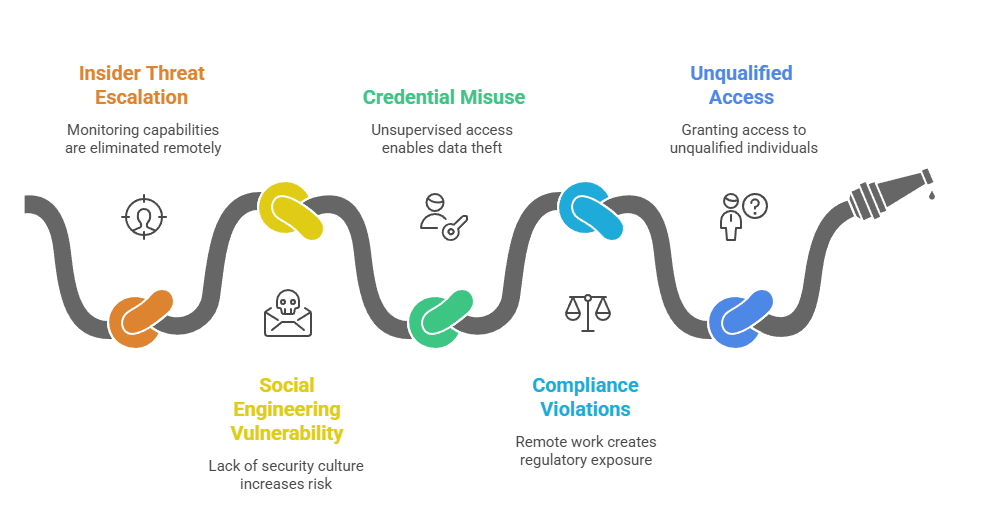
- Insider Threat Escalation: Remote environments eliminate behavioral monitoring capabilities. Background checks must identify candidates with financial distress, substance abuse issues, or undisclosed legal problems. Research consistently links these circumstances to insider threat probability.
- Social Engineering Vulnerability: Remote workers lack the informal security culture that office environments naturally provide. This makes them targets for personalized phishing campaigns. Business email compromise attacks exploit their isolation and reduced peer awareness.
- Credential Misuse: Unsupervised access to corporate systems increases opportunities for data theft. It also enables competitive intelligence gathering and fraudulent transactions. Background screening helps prevent these through criminal history analysis.
- Compliance Violations: Remote workers operating across jurisdictions create regulatory exposure. Organizations must verify location, professional licenses, and authorization to work from specific regions. Failure creates legal and security risks.
- Unqualified Access: Without verification of claimed credentials and experience, organizations risk granting system access to unqualified individuals. These individuals may lack the technical competency or security knowledge required for remote positions.
These vulnerabilities demonstrate why comprehensive remote employee background checks have transitioned to essential security controls. Organizations that recognize this imperative position themselves to capitalize on distributed talent. They simultaneously avoid costly security incidents that plague competitors with inadequate screening protocols.
Developing Comprehensive Work From Home Security Policies
Integrating Background Checks Into Security Frameworks
Work from home security policies must explicitly position background verification as a foundational security control. It should rank equivalent to firewalls, encryption, and access management. Security frameworks including NIST, ISO 27001, and CIS Controls classify personnel screening as essential controls.
Yet many organizations implement these standards without extending screening rigor to remote workers. Policy documentation should specify requirements clearly. All personnel with remote system access must undergo identical screening. This applies regardless of employment status, location, or contractor classification.
The timing of background checks relative to system access creates a critical security gap. Organizations often grant provisional access before screening completes. Virtual team risk management policies should mandate specific requirements. No system credentials, VPN access, or company devices should be provisioned until background checks are clear. This zero-trust approach prevents scenarios where candidates with disqualifying findings already possess network access during termination.
Continuous Monitoring and Rescreening Protocols
Initial remote employee background checks provide a point-in-time security assessment. This assessment degrades immediately as circumstances change. Continuous monitoring programs alert employers to criminal arrests and professional license suspensions. They also flag sanctions list additions indicating elevated security risk.
For remote workers operating unsupervised with persistent system access, ongoing monitoring becomes essential. It transitions from optional enhancement to critical security control. This enables rapid response to emerging threats that develop after initial hiring.
Periodic rescreening frequencies should align with position risk profiles. They must also match regulatory requirements and industry standards. Financial services organizations typically rescreen every 3-5 years. Healthcare entities follow similar intervals for HIPAA compliance.
Remote work security risks justify more frequent rescreening in many cases. The lack of supervision means behavioral changes go undetected. Office managers might observe these changes naturally. Instead, they remain hidden until they manifest as security incidents.
Remote Worker Onboarding Security Requirements
Secure onboarding for remote employees extends beyond traditional background verification to encompass security checkpoints that office environments naturally provide. Organizations must validate the individual's identity, qualifications, and home workspace security before granting full system access.
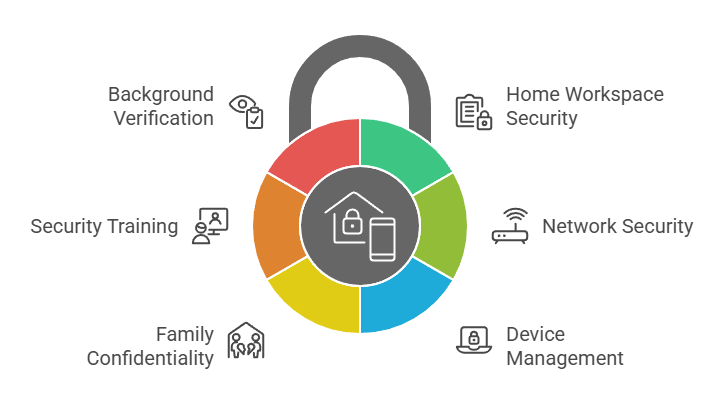
- Home Workspace Security Assessment: Questionnaires or inspections confirm lockable storage for documents, separated work areas from family spaces, and visual privacy during video conferences.
- Network Security Validation: Verification that home connections use WPA3 or WPA2 encryption, separate guest networks exist, and VPN requirements are understood.
- Device Management Enrollment: Company-owned devices with full-disk encryption, endpoint detection software, remote wipe capabilities, and mobile device management enrollment.
- Family Confidentiality Training: Documentation that household members understand confidentiality obligations, restrictions on discussing work, and prohibitions on accessing work devices.
- Security Training Completion: Mandatory training covering home network security, phishing recognition, document security, video conference security, and incident reporting.
- Background Check Clearance Verification: Automated systems blocking credential issuance until background checks clear, training completes, and device enrollment succeeds.
Organizations implementing comprehensive remote onboarding protocols report 42% fewer security incidents during the first 90 days of employment.
Legal Compliance in Remote Employee Background Checks
Federal and State Regulatory Requirements
Remote employee background checks must navigate complex regulatory requirements where federal, state, and international laws intersect. The Fair Credit Reporting Act (FCRA) provides the federal foundation requiring written authorization, disclosure, and adverse action procedures.
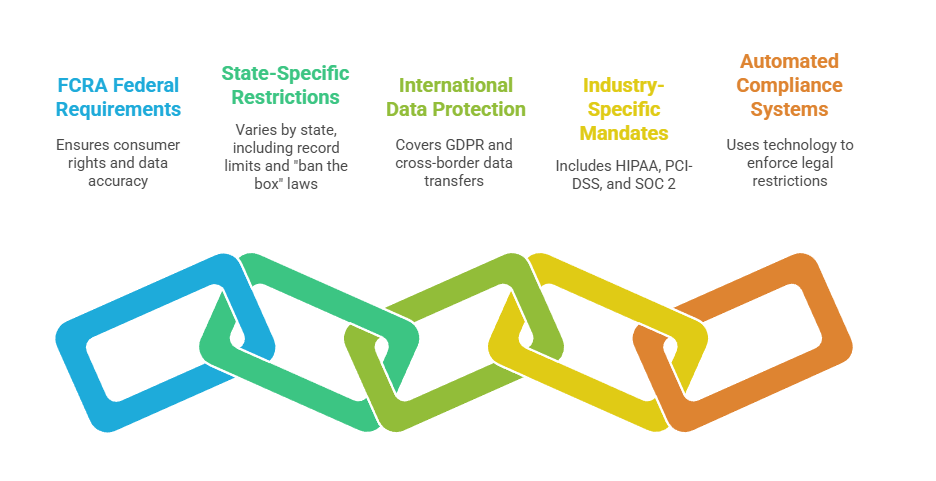
- FCRA Federal Requirements: Written authorization before checks, disclosure of consumer report use, pre-adverse action notices for disputes, and final adverse action notices with proper documentation.
- State-Specific Restrictions: California's seven-year criminal record limit, "ban the box" laws in 37 states, state credit report limitations, and varying statutes requiring location-specific protocols.
- International Data Protection: GDPR requirements for legitimate interest assessments, data minimization, explicit consent, erasure rights, and Standard Contractual Clauses for cross-border transfers.
- Industry-Specific Mandates: HIPAA for healthcare workers, PCI-DSS for cardholder data handlers, SOC 2 compliance frameworks, CMMC for defense contractors, and FINRA/SEC regulations.
- Automated Compliance Systems: Technology platforms applying legal restrictions based on location, position, and regulations while maintaining audit trails.
Organizations failing to maintain compliance face FCRA damages of $100-$1,000 per violation, class action litigation, and GDPR penalties reaching 4% of global revenue.
Documentation and Record Retention
Proper documentation protects organizations during audits and legal challenges. Records should include authorization forms, disclosure statements, and candidate acknowledgments. All communications regarding adverse findings must be preserved.
Retention periods vary by jurisdiction and regulation. Federal law requires maintaining records for specific periods. State laws may impose longer requirements. Organizations should implement systematic record management ensuring compliance while enabling efficient retrieval.
Technology Solutions and Cost Analysis for Remote Worker Verification
Modern Background Check Platforms
Modern background check technology enables rapid, compliant screening through integrated platforms. These solutions connect with applicant tracking systems and HR management software. They automate candidate consent workflows and order appropriate searches based on position risk profiles.
Screening progress monitoring occurs automatically. Compliant disclosure communications are generated systematically. For organizations managing distributed remote hiring, centralized platforms ensure consistency. Screening remains uniform regardless of hiring manager location. Audit trails demonstrate compliance during regulatory examinations.
API integrations between background check providers and HR technology stacks enable seamless data flow. This reduces manual handling of sensitive information. Automated systems can block credential provisioning until background checks are clear. They trigger rescreening based on employment anniversaries or position changes. Security teams receive alerts when continuous monitoring identifies concerning events.
Return on Investment Analysis
The investment in comprehensive remote employee background checks generates measurable returns. Reduced security incidents provide direct cost savings. Improved workforce quality enhances productivity. Enhanced regulatory compliance avoids penalties.
Organizations implementing rigorous screening protocols report significant improvements. They experience 58% fewer insider threat incidents. Negligent hiring liability decreases by 42%. Employee retention improves by 33%. These operational improvements translate to substantial cost avoidance. Benefits typically exceed background check expenses within the first year.
| Security Benefit | Impact Metric | Cost Avoidance |
| Reduced Data Breaches | 58% fewer insider incidents | $2.8M average per prevented breach |
| Improved Compliance | 72% fewer audit findings | $850K average remediation savings |
| Lower Turnover | 33% retention improvement | $45K average replacement cost per position |
| Decreased Liability | 42% fewer negligent hiring claims | $1.2M average settlement/judgment |
These metrics demonstrate that comprehensive screening delivers strategic advantages beyond cost avoidance. Organizations achieve improved cyber insurance positioning. They gain competitive differentiation in security-conscious industries. Enhanced reputation for security diligence attracts quality candidates. Regulatory compliance reduces audit burden and associated costs.
Building a Sustainable Remote Workforce Security Culture
Technology and policy frameworks provide necessary structure, but sustainable security requires cultural transformation. Employees must understand their role in threat prevention and view security as shared responsibility. Background checks serve as the first cultural touchpoint communicating security expectations from initial application.
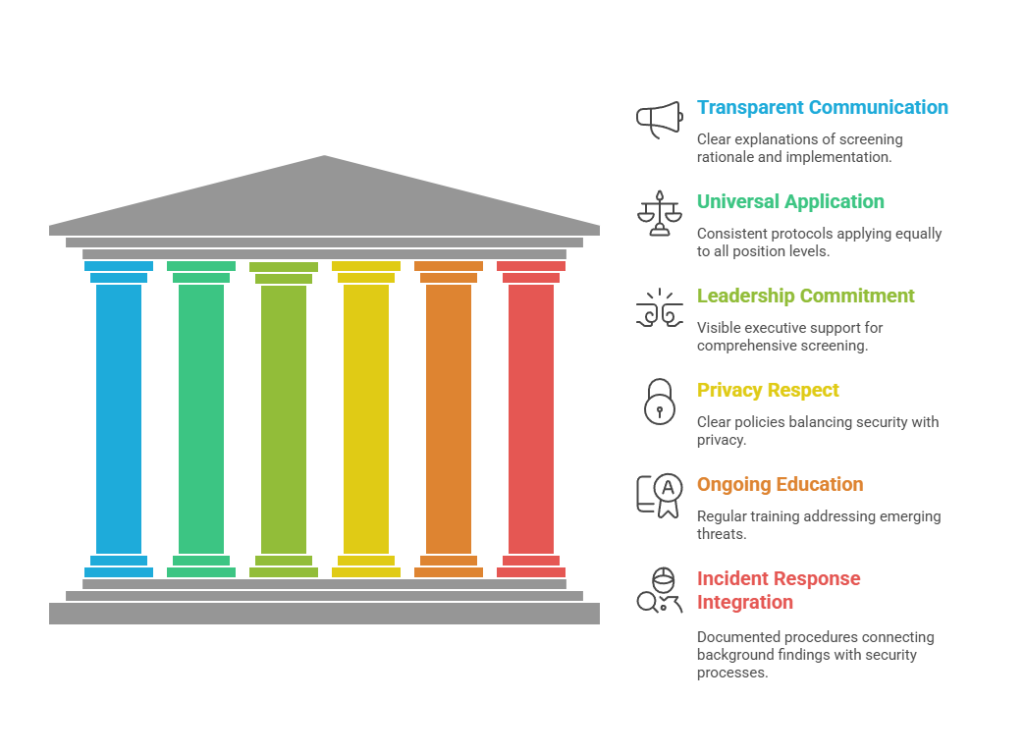
- Transparent Communication: Clear explanations of screening rationale and implementation demonstrating that checks protect all employees by ensuring colleagues meet security standards.
- Universal Application: Consistent protocols applying equally to all position levels regardless of urgency, demonstrating security as core value rather than conditional priority.
- Leadership Commitment: Visible executive support for comprehensive screening even during hiring pressure, preventing precedents that undermine policy effectiveness.
- Privacy Respect: Clear policies articulating what is checked, how information is used, retention practices, and candidate rights, balancing security with privacy.
- Ongoing Education: Regular training addressing emerging threats and reinforcing connections between screening and broader security objectives.
- Incident Response Integration: Documented procedures connecting background findings with security monitoring, investigation, and response processes.
Organizations with mature security cultures report 67% higher employee engagement in security initiatives including incident reporting and policy adherence. This transforms background checks from administrative requirement into strategic security enabler permeating all workforce management aspects.
Conclusion
Remote employee background checks constitute the foundational security control for virtual workforces. They address vulnerabilities that emerge when traditional physical security barriers disappear. As organizations finalize remote work strategies for 2025 and beyond, comprehensive background verification must transition from optional practice to mandatory protocol.
Integration with ongoing monitoring creates essential security infrastructure. The convergence of HR screening and IT security creates both compliance imperative and strategic opportunity. It enables organizations to build resilient remote workforces.
Organizations implementing rigorous remote worker verification position themselves advantageously. They capitalize on distributed talent while avoiding costly security incidents. Competitors with inadequate screening protocols face increasing risks and expenses in the evolving threat landscape.
Frequently Asked Questions
Remote work may have removed office walls, but it hasn’t removed the need for strong security and compliance. It has actually increased the importance of background screening. Here are a few of the most popular questions that are often asked in the process of either creating a new telecommuting employee background screening process or enhancing one that is already in place, from what is to be done during the process to how often a background screen is to be done on telecommuters worldwide.
What should be included in background checks for remote employees?
Remote employee background checks should include identity verification and criminal history searches covering all jurisdictions. Employment verification with previous employers is essential. Education credential validation and professional license verification when applicable provide additional security.
Reference checks should specifically address trustworthiness and performance in unsupervised settings. For positions accessing sensitive systems or data, additional components offer enhanced assurance. These include credit reports, continuous criminal monitoring, and social media analysis.
How often should remote workers be rescreened?
Remote workers should undergo comprehensive rescreening every 3-5 years at minimum. More frequent intervals apply for positions involving financial systems, regulated data, or administrative privileges. Continuous criminal monitoring should supplement periodic rescreening.
This provides real-time alerts about arrests, convictions, and other events between formal background checks. The specific rescreening frequency should align with regulatory requirements applicable to your industry. Position risk profiles and security framework standards also influence timing.
Are background check requirements different for remote workers versus office employees?
While fundamental background check components remain consistent, remote workers typically require enhanced screening scope. Unsupervised work-from-home environments create expanded security risks. Remote hiring security protocols should include additional verification of home workspace security.
Geographic location confirmation addresses jurisdictional concerns. More thorough reference checks specifically address remote work competency. The elevated trust required for remote system access justifies this enhanced verification approach.
What are the legal requirements for conducting remote employee background checks?
All employment background checks must comply with the Fair Credit Reporting Act (FCRA). This requires written authorization and disclosure of consumer report use. Adverse action procedures apply when unfavorable information influences hiring decisions.
State laws impose additional requirements including ban-the-box restrictions and salary history inquiry prohibitions. Limitations on criminal record consideration vary by state. Organizations hiring international remote workers must additionally comply with GDPR and UK GDPR. These regulations govern how personal information is collected and processed.
How do background checks address remote work security risks?
Remote employee background checks mitigate security risks by identifying candidates with problematic criminal histories. These may indicate propensity for fraud, data theft, or misconduct. Verification confirms that claimed credentials and experience are legitimate rather than fabricated.
Financial distress or other circumstances correlating with insider threat probability are uncovered. When integrated with continuous monitoring, background screening provides ongoing visibility. This reveals circumstances that might compromise remote worker trustworthiness.
What background check red flags are particularly concerning for remote positions?
Red flags especially concerning remote workers include any history of computer crimes, fraud, or identity theft. Financial misconduct indicates technical capability and willingness to misuse system access. Frequent job changes or unexplained employment gaps suggest instability.
Undisclosed terminations raise integrity concerns. Discrepancies between claimed credentials and verification results indicate dishonesty. Significant financial distress creates motivation for data theft or fraud.
Can background checks be conducted on international remote workers?
Yes, background checks can be conducted on international remote workers. However, they require navigation of data protection regulations including GDPR. Record availability varies across jurisdictions. Turnaround times are typically longer than domestic screening.
International background checks should verify identity, education credentials, and employment history. Criminal records should be checked to the extent available in the candidate's country. Organizations hiring internationally should partner with background screening providers experienced in global verification. Compliance with cross-border data transfer requirements is essential.
Additional Resources
- FCRA Compliance Guide for Employment Screening
https://www.ftc.gov/business-guidance/resources/using-consumer-reports-what-employers-need-know - NIST Special Publication 800-53: Security and Privacy Controls
https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/final - Remote Workforce Security Best Practices - CISA
https://www.cisa.gov/telework - State Background Check Laws and Requirements
https://www.nolo.com/legal-encyclopedia/state-laws-use-arrests-convictions-employment.html - GDPR Guidance on Employee Data Processing
https://gdpr.eu/data-privacy-in-the-workplace/

GCheck Editorial Team
Meet the GCheck Editorial Team, your trusted source for insightful and up-to-date information in the world of employment background checks. Committed to delivering the latest trends, best practices, and industry insights, our team is dedicated to keeping you informed.
With a passion for ensuring accuracy, compliance, and efficiency in background screening, we are your go-to experts in the field. Stay tuned for our comprehensive articles, guides, and analysis, designed to empower businesses and individuals with the knowledge they need to make informed decisions.
At GCheck, we're here to guide you through the complexities of background checks, every step of the way.






