Identity fraud in hiring encompasses multiple threat categories ranging from stolen identities to synthetic profiles and document forgery, each requiring distinct detection strategies and risk mitigation protocols. Organizations face increasing verification complexity as fraud techniques evolve, making systematic process design and staff training essential components of workforce integrity management.
Key Takeaways
- Identity fraud in hiring includes stolen identity use, synthetic identity creation, document forgery, credential fabrication, impersonation during interviews, work authorization fraud, and employment history misrepresentation, each carrying different risk profiles and detection requirements.
- Synthetic identities, which combine real and fabricated information, represent a growing challenge because they often pass automated verification systems while creating significant downstream liability exposure.
- Detection indicators vary by fraud type and hiring stage, requiring layered verification approaches that cross-reference multiple data sources rather than relying on single-point checks.
- Employers face both regulatory obligations for identity verification and discretionary risk management decisions that extend beyond minimum compliance thresholds.
- Common misconceptions, such as assuming E-Verify or background checks provide comprehensive fraud protection, create exploitable vulnerabilities in verification workflows.
- Remote hiring environments have amplified certain fraud vectors, particularly impersonation schemes and document forgery, requiring adapted authentication protocols.
- Organizations should implement risk-based verification approaches that match screening depth to role sensitivity, access levels, and regulatory requirements rather than applying uniform processes across all positions.
- Effective fraud prevention requires coordinated procedural design spanning resume review, interview protocols, document collection, background screening, and onboarding stages.
Understanding Identity Fraud in Hiring: Scope and Boundaries
Identity fraud in hiring occurs when an applicant misrepresents their identity through falsified credentials, stolen personal information, or fabricated identity elements to gain employment. This includes presenting false identification documents, using another person's identity credentials, creating synthetic identities that blend real and fabricated information, or engaging someone else to impersonate the actual applicant during interviews or assessments.
Distinguishing Related but Separate Issues
Resume fraud represents a different category focused on misrepresenting qualifications, experience, or educational achievements rather than identity itself. Employee-side identity theft, where a legitimate worker's personal information is compromised after hire, creates victim scenarios rather than perpetrator situations. Immigration law violations constitute a separate compliance domain with distinct regulatory frameworks, though work authorization fraud can intersect with identity fraud when false documents are used to establish eligibility.
Operational responses differ substantially based on fraud type. Identity fraud discovered during hiring typically results in application withdrawal or offer rescission with potential law enforcement notification. Post-hire discovery triggers termination procedures, regulatory reporting obligations, and security audits to assess information access during employment.
Fraud Type Taxonomy: Classification and Characteristics
Identity fraud in hiring manifests through distinct methodologies, each requiring specialized detection approaches and carrying unique risk profiles.
Stolen Identity Fraud
Stolen identity fraud occurs when perpetrators use another person's legitimate credentials, including Social Security numbers, dates of birth, and identification documents, to apply for employment. The actual identity holder typically remains unaware until credit monitoring alerts, tax filing conflicts, or background check inquiries reveal unauthorized employment activity.
This fraud type often involves organized criminal networks that acquire identity information through data breaches, phishing schemes, or physical document theft. Detection complexity arises because verification systems confirm the identity exists and credentials match, as they genuinely belong to a real person. The mismatch between the physical applicant and the identity holder only becomes apparent through biometric verification, in-person document examination, or background check anomalies.
Synthetic Identity Fraud
Synthetic identity fraud combines real information, typically a valid Social Security number, with fabricated biographical details to create a new identity that does not correspond to any actual person. Perpetrators often use Social Security numbers belonging to minors, deceased individuals, or recent immigrants whose credit histories remain undeveloped.
This approach has gained sophistication as fraudsters establish credit histories for synthetic identities over months or years before deploying them in employment contexts. The synthetic identity may pass E-Verify and basic background checks because the Social Security number validates, even though the associated name, address, and employment history are fabricated.
Document Forgery and Alteration
| Document Type | Common Forgery Methods | Detection Challenges |
| Driver's Licenses | High-quality printing, lamination, hologram replication | Sophisticated forgeries replicate security features requiring specialized equipment |
| Social Security Cards | Template manipulation, card stock printing | Material composition differences detectable only through physical examination |
| Immigration Documents | Security feature reproduction, photograph substitution | Remote review cannot capture UV-reactive elements or tactile features |
| Educational Credentials | Institutional template copying, seal fabrication | Diploma mills produce realistic documents requiring direct registrar verification |
Technology advances have reduced the specialized skills previously required, with high-quality printers and design software enabling convincing replicas. Detection requires document authentication knowledge that most HR personnel do not possess through routine training.
Credential Fabrication
Credential fabrication encompasses fake educational degrees, professional certifications, and licenses. Diploma mills produce realistic-looking degrees from non-existent or unaccredited institutions, while sophisticated operations create documents purporting to come from legitimate universities.
This fraud type intersects with identity fraud when supporting documents such as transcripts, certification cards, or license numbers are fabricated to create a verifiable paper trail. The risk escalates significantly in regulated industries where specific credentials constitute legal prerequisites for employment.
Impersonation Fraud
Impersonation fraud occurs when someone other than the actual applicant participates in interviews, assessments, or verification processes. Remote hiring environments have amplified this risk by removing in-person identity confirmation touchpoints that previously existed in traditional hiring workflows.
Schemes range from simple scenarios where a more qualified friend completes a video interview to sophisticated operations involving professional impersonators. The actual applicant appears for in-person onboarding or may continue the impersonation indefinitely while another individual performs the work.
Work Authorization Fraud
Work authorization fraud involves misrepresenting employment eligibility through false claims of citizenship, permanent residence, or work visa status. This category includes presenting forged immigration documents, using another person's work authorization credentials, or providing false information during I-9 completion.
This fraud type creates distinct legal exposure because it directly implicates immigration law compliance, with potential penalties including fines, loss of government contracting eligibility, and in extreme cases, criminal charges.
Reference and Employment History Fabrication
Reference fraud involves creating fictional employment histories with supporting verification infrastructure. Sophisticated schemes establish fake companies with websites, business listings, and answering services that confirm fabricated employment when contacted by background screeners.
This category serves as an identity-adjacent fraud type because it constructs a false professional identity. The intersection occurs when fabricated employment histories include forged identification documents such as employee badges, pay stubs, or W-2 forms used to substantiate claims.
Risk Profile by Fraud Type
| Fraud Type | Consequence Level | Detection Difficulty | Primary Risks |
| Stolen Identity | High | Moderate | Direct victim harm, tax complications, legal liability |
| Synthetic Identity | High | High | Regulatory violations, system access by unknown actors |
| Document Forgery | Variable | High | Depends on what fraud conceals |
| Credential Fabrication | Moderate to High | Moderate | Patient harm in healthcare, regulatory sanctions in regulated sectors |
| Impersonation | Moderate to High | High | Performance gaps, security exposure if continuing post-hire |
| Work Authorization | High | Variable | Immigration law penalties, contracting eligibility loss |
| Employment History Fabrication | Low to Moderate | Low to Moderate | Performance issues, potential concealment of serious conduct |
Understanding the relative threat levels enables risk-based resource allocation and proportionate response protocols. Stolen identity fraud carries severe consequences because it creates direct victims whose financial and legal standing may be compromised. Synthetic identities represent increasing risk because detection difficulty remains high even with standard verification procedures.
Detection Indicators and Red Flags
Identifying identity fraud requires systematic observation across multiple hiring stages, with specific indicators varying by fraud type and organizational verification capabilities.
Resume and Application Stage
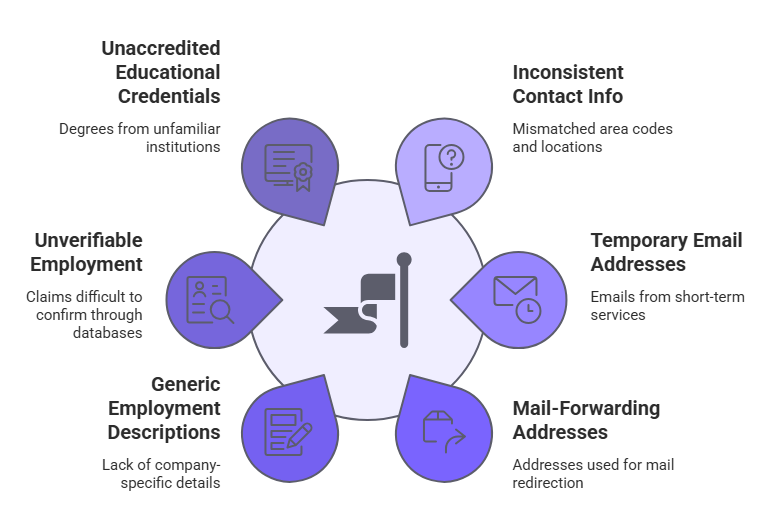
- Inconsistent contact information such as mismatched area codes between phone numbers and stated locations
- Email addresses from temporary services rather than established providers
- Addresses associated with mail-forwarding businesses
- Generic employment descriptions with minimal company-specific detail
- Employment claims at organizations difficult to verify through standard business databases
- Educational credentials from unfamiliar institutions lacking regional accreditation
Interview Stage Indicators
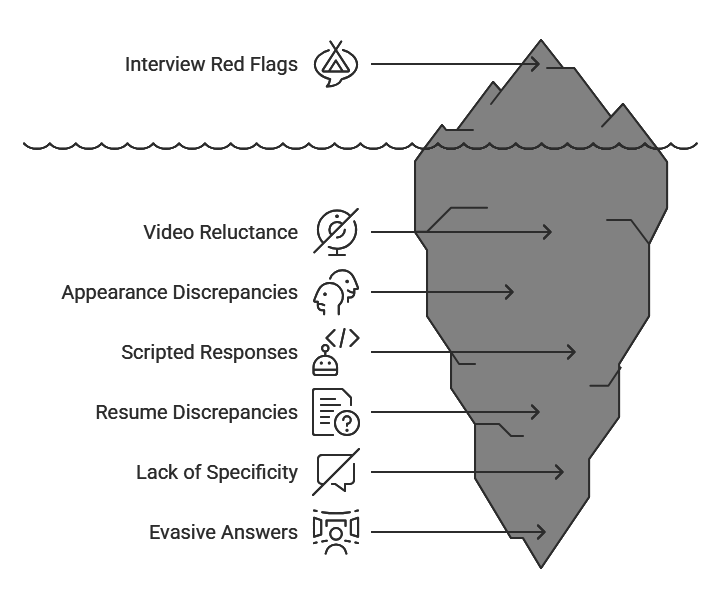
- Candidate reluctance to enable video during virtual interviews or persistent technical issues affecting video quality
- Noticeable differences between application photos and interview appearance
- Responses that seem scripted or delayed in ways suggesting off-camera coaching
- Significant discrepancies between resume claims and interview responses about employment responsibilities
- Inability to provide specific examples or contextual details about claimed experiences
- Evasive responses to questions about employment verification or reference contacts
Document Collection and Background Check Stage
Identification documents displaying visible irregularities such as font inconsistencies, misaligned text, incorrect document formats, or missing security features require expert review. Reluctance to present original documents in person or submission of poor-quality images that obscure security features may indicate document fraud.
Background checks returning no information on an adult applicant beyond minimal public records may indicate synthetic identities. Employment verification that produces businesses with minimal online presence or verification contacts using personal email addresses raises concerns.
Cross-Reference Verification Indicators
Inconsistencies across multiple data points create stronger fraud indicators:
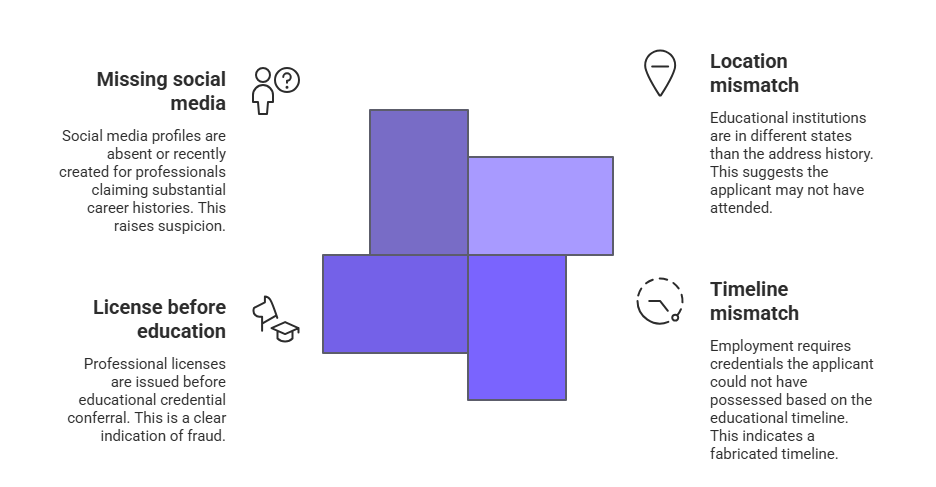
- Educational institutions located in different states than address history during claimed attendance periods
- Employment requiring credentials the applicant could not have possessed based on educational timeline
- Professional licenses issued before educational credential conferral
- Social media profiles absent or recently created for professionals claiming substantial career histories
Regulatory and Legal Context
Employers operate within defined legal frameworks establishing minimum identity verification obligations while retaining discretion to implement enhanced procedures based on risk management priorities.
I-9 Compliance Requirements
Immigration Reform and Control Act provisions require employers to verify identity and employment authorization for all employees through Form I-9 completion within three business days of the employee's first day of work for pay. Employers must examine original documents from I-9 acceptable document lists and determine whether documents reasonably appear genuine.
Regulations prohibit employers from specifying which acceptable documents employees must provide, rejecting documents that reasonably appear genuine, or requiring additional documentation beyond I-9 requirements based on national origin or citizenship status. Employers may request additional documentation only when applied uniformly to all employees in similar circumstances or when legitimate verification concerns exist independent of protected characteristics.
Liability protections exist for employers who accept documents that reasonably appear genuine on their face, even if later proven fraudulent, provided the employer completed I-9 procedures in good faith.
E-Verify Framework
E-Verify provides electronic employment eligibility verification by comparing I-9 information against Social Security Administration and Department of Homeland Security databases. The system confirms whether employee-provided information matches government records but does not authenticate documents or verify the person presenting documents is the legitimate holder of that identity.
FCRA Application to Fraud Detection
The Fair Credit Reporting Act regulates background checks conducted by consumer reporting agencies, requiring employers to provide clear written disclosure in a standalone document, obtain written authorization from the candidate, and follow adverse action procedures when background check information contributes to employment decisions.
Background checks that surface identity discrepancies trigger FCRA protections, requiring pre-adverse action notification, opportunity to dispute inaccurate information, and final adverse action notice.
State and Local Considerations
Some state laws create additional requirements for specific industries, roles, or employer types. Certain states impose enhanced verification obligations for healthcare facilities, financial institutions, or positions involving vulnerable populations beyond federal minimums. Requirements vary significantly by jurisdiction, and employers should verify obligations specific to their operating locations.
Ban-the-box legislation in numerous jurisdictions restricts when and how employers may inquire about criminal history. These laws vary significantly by location, with some affecting only initial applications while others extend to later hiring stages and require individualized assessments. Employers should verify requirements in their specific jurisdiction, particularly when identity verification surfaces discrepancies that may relate to criminal record concerns.
Data breach notification laws become relevant when identity fraud discovery reveals potential compromise of other employees' information or when fraudsters accessed systems containing protected data. Negligent hiring claims create potential liability when employers fail to conduct reasonable verification and employees subsequently harm third parties in ways foreseeable through adequate screening.
Operational Process Design
Effective identity fraud prevention requires integrated verification workflows spanning application through onboarding, with coordinated touchpoints that cross-reference information and create multiple fraud detection opportunities.
Layered Verification Architecture
Single-point verification creates vulnerability because sophisticated fraud may defeat individual checks. Layered approaches implement several independent verification mechanisms:
- Initial: Automated screening for application completeness, logical consistency in timelines, preliminary database queries
- Intermediate: Interview-stage behavioral observation, detailed questioning about claimed experiences, preliminary reference checks
- Final: Comprehensive background checks, credential verification through issuing institutions, in-person document authentication, cross-reference analysis
Document Authentication Protocols
Effective document authentication requires training HR personnel to recognize common security features and irregularities. Physical examination protocols include verifying document thickness, examining printing quality, checking security features under UV light when available, and comparing presented documents to reference guides.
Remote verification requires high-resolution imaging, multiple-angle photography, and potentially video presentation allowing real-time examination.
Background Check Integration and Conditional Offers
Background check timing affects fraud detection effectiveness. Comprehensive screening should include identity verification confirming Social Security number validity, employment verification contacting claimed employers directly, educational verification through institutional registrars, and structured reference checks.
Conditional offer practices protect organizations while enabling thorough verification. Offers should explicitly state employment contingency on satisfactory verification completion. Suspected fraud requires careful handling to avoid defamation exposure. Communication should focus on inability to verify information rather than fraud accusations.
Escalation and Investigation Protocols
| Stage | Action | Decision Authority |
| Initial Suspicion | Document concerns, notify HR | Hiring Manager/Recruiter |
| HR Evaluation | Assess evidence, consult legal counsel | HR Director |
| Enhanced Screening | Request additional verification, contact background check vendor | HR/Compliance |
| Law Enforcement Notification | Report suspected criminal activity | Legal Counsel/Executive Leadership |
Common Misconceptions and False Confidence
Overconfidence in existing verification procedures creates exploitable vulnerabilities based on incomplete understanding of verification limitations.
E-Verify as Comprehensive Protection
Organizations participating in E-Verify sometimes assume the system provides comprehensive fraud protection, when it actually confirms only that provided Social Security numbers match government records. Stolen identities using legitimate credentials produce confirmation results, as do synthetic identities with valid Social Security numbers paired with fabricated biographical details.
Visual Document Inspection Confidence
Many organizations assume HR staff can identify fraudulent documents through visual inspection, underestimating forgery sophistication. Sophisticated forgeries replicate security features to degrees requiring specialized equipment and expertise to identify. Remote document review compounds this limitation.
Background Check Comprehensiveness
Background checks provide valuable verification but operate within limitations. Checks confirm information present in databases but may not reveal fabricated employment at small businesses, international credentials difficult to verify remotely, or synthetic identities with insufficient history to generate findings.
Additional Misconceptions
Small and mid-sized organizations sometimes assume identity fraud targets only large employers, yet smaller organizations often maintain less sophisticated verification procedures. All organizations face fraud risk proportionate to their hiring volume and position sensitivity rather than size.
While remote hiring has created new fraud vectors, traditional in-person hiring had significant vulnerabilities. Remote hiring requires adapted protocols but can achieve comparable verification through systematic cross-reference procedures.
Emerging Fraud Vectors and 2026 Operational Realities
The identity fraud landscape has evolved materially through technological developments, workforce changes, and fraud technique sophistication.
AI-Assisted Document Generation
Artificial intelligence tools have reduced the technical skill required to produce convincing forged documents. Image generation capabilities allow fraudsters to create realistic identification documents and credentials with minimal expertise.
Operational responses include enhanced document authentication during in-person onboarding, direct verification with issuing institutions, and cross-reference checking to identify inconsistencies.
Remote Hiring at Scale
Organizations conducting high-volume remote hiring face fraud risk amplification through reduced personal interaction touchpoints. Organizations should implement adapted verification including video interview recording, multiple interviewer involvement, systematic employment verification procedures, and periodic video interaction requirements.
Synthetic Identity Sophistication
Fraudsters establish synthetic identities months or years before employment use, building credit histories that make the synthetic identity appear legitimate. Detection requires verification approaches that confirm identity legitimacy rather than merely checking for negative information.
Decision Framework for Prevention Investment
Organizations evaluating identity fraud prevention approaches benefit from structured assessment of exposure and resource allocation appropriate to risk profile.
Organizational Exposure Assessment and Verification Depth
Exposure assessment begins with position inventory categorizing roles by identity fraud risk factors including work authorization requirements, credential prerequisites, access to sensitive information, financial system access, and regulatory compliance responsibilities.
| Position Risk Level | Verification Components | Typical Roles |
| High-Risk | Comprehensive employment history, credential verification through registrars, professional license verification, enhanced background checks | Healthcare providers, financial advisors, compliance officers |
| Moderate-Risk | Most recent employment verification, degree confirmation, standard background checks, reference checks | General office positions, customer service, technical roles |
| Entry-Level | Basic background check, most recent employment verification, credential verification for requirements | Administrative support, hourly positions, limited-access roles |
Process vs. Technology Investment
Process improvements including staff training, verification procedure documentation, and quality assurance reviews provide foundational fraud prevention. Technology investments may include document authentication equipment and verification software. External services including background check providers and credential verification specialists offer expertise most organizations cannot develop internally cost-effectively.
Business Case Development
Business cases for fraud prevention investment should quantify costs of fraud incidents including wages paid to fraudulent employees, termination and replacement costs, legal expenses, regulatory penalties, and reputation damage. Prevention investment should also consider compliance value beyond fraud detection, including FCRA requirements, I-9 obligations, and state law compliance.
Conclusion
Identity fraud in hiring encompasses multiple distinct threat categories requiring systematic verification approaches matched to organizational risk profiles. Effective prevention combines trained personnel, layered verification protocols, appropriate technology, and external expertise where needed. Organizations should consult with legal counsel and compliance professionals to ensure verification procedures meet applicable federal, state, and local requirements for their specific circumstances.
Frequently Asked Questions
What is the difference between identity fraud and resume fraud in hiring?
Identity fraud involves misrepresenting who a person is through stolen credentials or forged documents, while resume fraud misrepresents qualifications without necessarily concealing identity. Identity fraud creates legal exposure related to work authorization and background check validity. Detection methods, legal frameworks, and organizational responses differ substantially between these categories.
How can employers detect synthetic identity fraud during hiring?
Synthetic identity detection requires verification that confirms identity legitimacy rather than merely checking for negative information. Indicators include background checks returning minimal information inconsistent with claimed work history and Social Security numbers showing issuance patterns inconsistent with stated age. Direct verification with claimed employers and educational institutions provides stronger detection than database queries alone.
Are employers legally required to detect identity fraud beyond basic I-9 compliance?
Federal law requires employers to complete I-9 verification and accept documents that reasonably appear genuine but does not mandate fraud detection beyond this standard. However, industry-specific regulations may impose enhanced verification requirements. Organizations should assess position-specific risks and regulatory requirements rather than assuming minimum compliance provides adequate protection.
Does E-Verify prevent all work authorization fraud?
E-Verify confirms that provided Social Security numbers match government records but does not authenticate physical documents or verify the person presenting credentials is the legitimate holder. The system reduces work authorization fraud risk substantially but remains vulnerable to sophisticated document forgeries and stolen identities using legitimate credentials.
What red flags indicate possible impersonation fraud during remote interviews?
Impersonation indicators include candidate reluctance to enable video, persistent technical issues affecting video quality, noticeable differences between application materials and interview appearance, and responses suggesting off-camera coaching. Organizations should implement multiple-interviewer processes and conduct interviews at different times to increase impersonation difficulty.
How should employers handle suspected identity fraud without facing defamation claims?
Organizations should focus on objective verification failures rather than fraud accusations. Communication should state inability to verify claimed credentials rather than asserting fraud occurred. Documentation should record specific inconsistencies and verification attempts without subjective fraud conclusions. Legal counsel consultation is appropriate before making external fraud reports.
What verification approaches work for fully remote hiring processes?
Remote hiring verification should include high-resolution document imaging from multiple angles, systematic employment verification contacting claimed employers directly, educational credential verification through institutional registrars, and multiple-stage video interviews with different personnel. Organizations can implement in-person document authentication during onboarding even for remote positions.
Should small organizations invest in sophisticated identity verification procedures?
All organizations require basic verification appropriate to position sensitivity regardless of size. Small employers hiring for positions requiring specific credentials or involving financial authority face meaningful fraud risks warranting thorough verification. Resource constraints can be addressed through external background check services and risk-based approaches focusing enhanced verification on high-risk positions.
Additional Resources
- Form I-9, Employment Eligibility Verification
https://www.uscis.gov/i-9 - E-Verify Program Information
https://www.e-verify.gov/ - FCRA Summary of Rights
https://www.consumer.ftc.gov/articles/pdf-0096-fair-credit-reporting-act.pdf - Federal Trade Commission Identity Theft Resources
https://www.identitytheft.gov/ - Social Security Number Verification Service
https://www.ssa.gov/employer/ssnv.htm

GCheck Editorial Team
Meet the GCheck Editorial Team, your trusted source for insightful and up-to-date information in the world of employment background checks. Committed to delivering the latest trends, best practices, and industry insights, our team is dedicated to keeping you informed.
With a passion for ensuring accuracy, compliance, and efficiency in background screening, we are your go-to experts in the field. Stay tuned for our comprehensive articles, guides, and analysis, designed to empower businesses and individuals with the knowledge they need to make informed decisions.
At GCheck, we're here to guide you through the complexities of background checks, every step of the way.





