Arizona data center employers must navigate complex federal and state background check requirements, including FCRA compliance, DHS CFATS security protocols, and specialized energy infrastructure screening from SRP and APS utilities. The state's unique regulatory landscape, featuring indefinite criminal history reporting and "ban the box" policies for public employers, creates both opportunities and challenges for job seekers and hiring managers in this critical infrastructure sector.
Key Takeaways
- Arizona data centers require multi-tier background investigations covering criminal history, employment verification, educational credentials, professional certifications, and identity confirmation due to critical infrastructure protection needs.
- Federal compliance includes FCRA regulations, DHS CFATS security standards, and enhanced FBI fingerprint checks for roles involving sensitive operations or security clearances.
- Arizona's "ban the box" Executive Order 2017-07 prohibits public sector employers from asking about criminal history on initial applications, though private employers retain more flexibility in their screening timing.
- SRP and APS energy providers impose additional cybersecurity-focused background requirements, including financial stability assessments and online presence screenings for infrastructure-related positions.
- Standard background checks cost $25-$50 and take 3-7 business days, while enhanced security clearance investigations can exceed $15,000 and require 30-90 days or longer.
- Job seekers should proactively obtain personal background reports, gather supporting documentation, and prepare transparent explanations for any potential red flags to navigate Arizona's comprehensive vetting process successfully.
Understanding Arizona Data Center Background Check Framework
Arizona's data center industry operates under stringent security requirements that demand comprehensive employee vetting. The state's position as a growing technology hub, combined with its role in supporting critical infrastructure, creates a regulatory environment where background checks serve as the first line of defense against security threats. Data centers in Arizona must balance federal mandates, state-specific laws, and industry best practices to ensure proper screening protocols.
The complexity of Arizona data center background check requirements stems from multiple overlapping jurisdictions and security frameworks. Federal agencies like the Department of Homeland Security establish baseline security standards through programs like CFATS, while state regulations add layers of privacy protection and anti-discrimination measures. Energy providers such as Salt River Project and Arizona Public Service introduce additional screening requirements for facilities connected to the electrical grid.
Modern data centers handle sensitive information ranging from personal data to classified government communications, making thorough background screening essential for operational security. Arizona employers must verify not only criminal history but also professional qualifications, financial stability, and personal integrity. This comprehensive approach helps prevent insider threats while ensuring compliance with various regulatory frameworks governing critical infrastructure protection.
Core Components of Arizona Data Center Screening
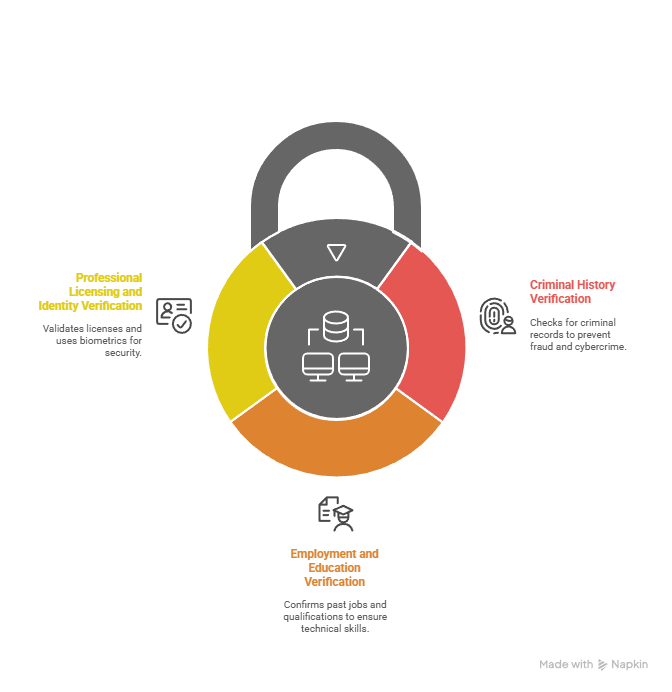
Criminal History Verification
Arizona data centers conduct extensive criminal background investigations across multiple jurisdictional levels. Employers search local, state, and federal databases to identify any criminal history that might pose security risks to sensitive operations. The state's indefinite criminal history reporting under FCRA guidelines allows employers to access comprehensive records without time limitations, though they must balance thoroughness with fairness in hiring decisions.
The screening process typically begins with name-based searches through county court records, followed by state-level database queries and federal background investigations. Violent crimes, financial fraud, cybercrime, and drug-related offenses receive particular scrutiny due to their potential impact on data center security. Employers must provide adverse action notices when criminal history influences hiring decisions, giving candidates opportunities to dispute inaccuracies or provide context for past incidents.
Recent technological advances have improved the accuracy and speed of criminal background verification. Automated systems can cross-reference multiple databases simultaneously, reducing processing times while increasing the likelihood of discovering relevant records. However, employers must remain vigilant about false positives and ensure proper verification of any concerning findings before making final hiring decisions.
Employment and Education Verification
Data center positions require specific technical skills and educational backgrounds, making employment and education verification critical components of the screening process. Employers contact previous supervisors, HR departments, and educational institutions to confirm job titles, employment dates, reasons for departure, and degree completions. Technical certifications from organizations like CompTIA, Cisco, and Microsoft receive special attention due to their relevance to data center operations.
| Verification Type | Timeline | Common Issues |
| Employment History | 3-5 business days | Closed businesses, unresponsive contacts |
| Education Records | 5-7 business days | International credentials, discontinued programs |
| Professional Certifications | 2-3 business days | Expired credentials, fraudulent claims |
The verification process can encounter delays when contacting international institutions, closed businesses, or unresponsive references. Candidates can expedite screening by providing complete contact information, official transcripts, and certification documentation. Employers increasingly use third-party verification services that maintain relationships with educational institutions and former employers to streamline the process.
Professional Licensing and Identity Verification
Arizona data centers require stringent identity verification to prevent unauthorized access to sensitive facilities and information. The process includes Social Security number validation, address history reviews, and work authorization confirmation. For foreign nationals, employers must verify current visa status and work permit validity through E-Verify and other government databases.
Professional licensing verification ensures candidates possess necessary industry certifications and maintain good standing with relevant regulatory bodies. Data center employers frequently verify:
- Technical Certifications: CompTIA A+, Network+, Security+, CISSP credentials
- Industry Licenses: Electrical, HVAC, and facility management certifications
- Security Clearances: Department of Defense and other federal clearance levels
- Professional Memberships: IEEE, AFCOM, and other industry organizations
Identity verification has become more sophisticated with biometric technology integration. Fingerprinting and facial recognition systems add security layers while reducing identity fraud risks. These technologies are particularly important in data centers where physical security measures must complement digital access controls.
Federal Security Requirements and Compliance
DHS CFATS Implementation
The Department of Homeland Security's Chemical Facility Anti-Terrorism Standards significantly impact data center security protocols in Arizona. While CFATS primarily targets chemical facilities, many data centers fall under these regulations due to their use of hazardous materials in cooling systems, backup power generation, and fire suppression systems. Facilities subject to CFATS must develop comprehensive security plans addressing personnel screening, access controls, and threat mitigation strategies.
Enhanced background checks under CFATS requirements extend beyond standard criminal history verification. FBI fingerprint checks become mandatory for personnel with access to sensitive areas or critical systems. These investigations examine not only criminal records but also associations, financial stability, and potential foreign influence. The process can take several months and may require interim security measures for new employees awaiting clearance completion.
CFATS compliance creates ongoing obligations for data center operators, including regular security plan updates, employee revalidation, and incident reporting. Arizona facilities must maintain detailed records of all background check activities and demonstrate continuous compliance with evolving security standards. Non-compliance can result in significant penalties and operational disruptions.
NERC CIP Standards
North American Electric Reliability Corporation Critical Infrastructure Protection standards apply to Arizona data centers connected to the bulk electric system. These facilities must implement comprehensive personnel risk assessments that go beyond traditional background checks. NERC CIP requirements include:
Personnel Risk Assessment Components:
- Identity Verification: Multi-source confirmation of personal identity
- Criminal History: Comprehensive seven-year lookback period
- Employment History: Detailed verification of previous positions
- Financial Assessment: Review of credit history and financial obligations
- Character References: Interviews with personal and professional contacts
NERC CIP compliance requires annual revalidation of personnel risk assessments, creating ongoing screening obligations for covered facilities. The standards also mandate specific access controls, training requirements, and incident response procedures that affect background check implementation.
Arizona-Specific Regulatory Requirements
"Ban the Box" Executive Order Implementation
Arizona Executive Order 2017-07 prohibits public sector employers from inquiring about criminal history on initial job applications. This policy aims to provide fair opportunities for individuals with criminal records by emphasizing qualifications over past convictions. However, the order only applies to public sector positions, leaving private data center employers with greater flexibility in their screening approaches.
The implementation of "ban the box" policies creates timing considerations for background check processes. Public employers must wait until after conditional job offers before conducting criminal history investigations. This approach can extend hiring timelines but may improve candidate pool diversity by reducing early-stage screening barriers.
Private sector data center employers in Arizona aren't bound by "ban the box" restrictions but may adopt similar practices voluntarily. Some companies find that delaying criminal history discussions until later in the hiring process improves their ability to evaluate candidates holistically rather than making premature disqualifications based solely on criminal records.
State Criminal History Reporting Standards
Arizona's approach to criminal history reporting differs significantly from many other states. The state permits indefinite reporting of criminal convictions under FCRA guidelines, meaning background checks can reveal criminal records from any point in an individual's history without time limitations. This comprehensive approach provides employers with extensive information but requires careful consideration to avoid unfair bias against candidates with older convictions.
Arizona Criminal History Reporting Framework:
| Record Type | Reporting Period | Considerations |
| Felony Convictions | Indefinite | No time limitations under state law |
| Misdemeanor Convictions | Indefinite | Subject to relevance and job requirements |
| Arrests Without Conviction | Limited use | Cannot be primary basis for disqualification |
| Sealed/Expunged Records | Generally excluded | May appear in federal security clearance checks |
The indefinite reporting standard requires employers to evaluate the relevance of older criminal records to current job responsibilities. Factors such as the nature of the offense, time elapsed since conviction, evidence of rehabilitation, and job-relatedness all influence appropriate consideration of criminal history information.
Energy Infrastructure Background Requirements
SRP Security Protocols
Salt River Project imposes specialized background check requirements for data centers receiving power from their grid infrastructure. These requirements focus on cybersecurity risks and insider threat prevention, reflecting the critical nature of power system operations. SRP's screening protocols include comprehensive financial background investigations to identify potential vulnerabilities that could compromise electrical grid security.
SRP requires compliance with North American Electric Reliability Corporation Critical Infrastructure Protection standards for applicable facilities. This compliance includes detailed personnel screening that examines criminal history, employment background, and personal associations. The utility also conducts periodic revalidation of background clearances to ensure ongoing personnel reliability.
Financial stability assessments form a crucial component of SRP's background requirements. The utility examines credit histories, bankruptcy filings, and significant debts that might create security risks. These investigations help identify individuals who might be susceptible to compromise due to financial pressures or foreign influence attempts.
APS Cybersecurity Screening
Arizona Public Service implements comprehensive cybersecurity-focused background screening for data center personnel with access to grid-connected systems. These investigations extend beyond traditional criminal history checks to include online presence verification, social media screening, and digital footprint analysis. APS recognizes that modern security threats often originate from digital channels requiring enhanced personnel vetting.
The utility's screening process includes specialized cybersecurity assessments that evaluate candidates' potential exposure to cyber threats. This includes reviewing online activities, professional associations, and technical certifications relevant to cybersecurity roles. APS also conducts ongoing monitoring of personnel with access to critical systems, creating continuous security awareness rather than one-time screening events.
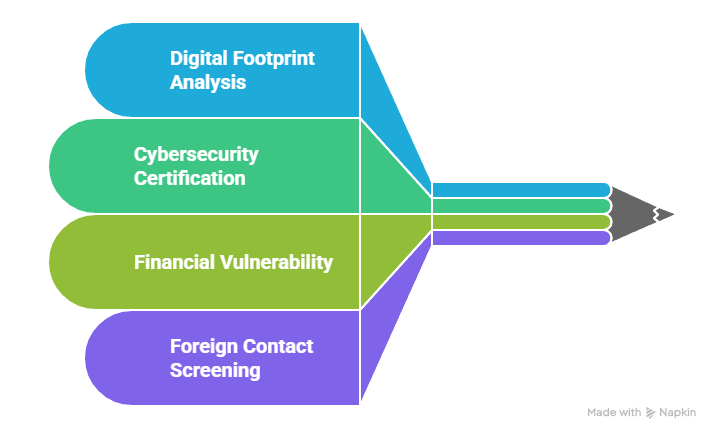
APS Enhanced Screening Elements:
- Digital Footprint Analysis: Social media and online presence review
- Cybersecurity Certification Verification: Current status of relevant certifications
- Financial Vulnerability Assessment: Comprehensive credit and debt analysis
- Foreign Contact Screening: Review of international associations and travel
Background Check Process Timelines and Costs
Standard Processing Expectations
Most Arizona data center background checks follow predictable timelines based on the complexity and scope of investigations required. Standard screenings typically complete within 3-7 business days and cost between $25-$50 per candidate. These investigations cover basic identity verification, criminal history searches, and employment confirmation sufficient for entry-level positions without security clearance requirements.
The efficiency of standard background checks has improved significantly with technological advances and digital database integration. Automated systems can process multiple verification requests simultaneously, reducing manual processing delays. However, complications such as incomplete candidate information, unresponsive references, or conflicting records can extend timelines beyond standard expectations.
Employers can optimize standard background check timelines by ensuring candidates provide complete, accurate information and necessary documentation upfront. Pre-employment preparation, including gathering employment records and contact information, can prevent common delays that extend the screening process unnecessarily.
Enhanced Security Clearance Processing
Federal security clearances required for sensitive data center positions involve substantially longer processing times and higher costs. These investigations can take 30-90 days or longer, with expenses ranging from several hundred to over $15,000 depending on clearance levels and investigation complexity. The extended timeline reflects comprehensive investigation procedures including interviews, reference checks, and federal database searches.
Enhanced clearance processing involves multiple government agencies and contractor organizations, creating coordination challenges that can extend timelines unpredictably. Factors such as international travel history, foreign contacts, or complex employment backgrounds may trigger additional investigation requirements. Candidates requiring clearances should expect interim security measures while awaiting final adjudication.
Clearance Processing Timeline Factors:
- Investigation Complexity: International elements extend processing time
- Agency Workload: Federal processing backlogs affect completion dates
- Candidate Cooperation: Responsive candidates expedite investigations
- Reference Availability: Difficult-to-reach references create delays
The investment in enhanced security clearances reflects their long-term value for both employers and employees. Cleared personnel often command higher salaries and enjoy greater career opportunities within the federal contracting community and critical infrastructure sectors.
Common Disqualifying Factors and Risk Assessment
Arizona data center employers evaluate multiple risk factors when making hiring decisions based on background check results. The assessment process considers not only the presence of concerning information but also its relevance to job responsibilities, timeframe, and evidence of rehabilitation or changed circumstances.
Primary Disqualification Categories:
- Violent Criminal History: Assault, domestic violence, and threats against persons
- Financial Crimes: Fraud, embezzlement, identity theft, and money laundering
- Cybercrime Convictions: Computer fraud, data theft, and network intrusions
- Substance Abuse Issues: Recent drug convictions and alcohol-related incidents
- Employment History Problems: Termination for cause, falsified credentials, and chronic job instability
- Financial Instability: Significant unpaid debts, recent bankruptcies, and poor credit management
The evaluation process requires balancing legitimate security concerns with fair employment practices. Employers must demonstrate that disqualification decisions relate directly to job requirements and consider factors such as time elapsed since incidents, evidence of rehabilitation, and overall candidate qualifications. This balanced approach helps ensure both security and compliance with anti-discrimination laws.
Risk assessment in data center hiring has evolved to include emerging threat vectors such as social engineering susceptibility and digital security awareness. Modern background investigations may include assessments of candidates' cybersecurity knowledge and their potential vulnerability to manipulation attempts that could compromise facility security.
Legal Protections and Candidate Rights
FCRA Compliance Framework
The Fair Credit Reporting Act provides comprehensive protections for job candidates undergoing background screening in Arizona. Employers must obtain written consent before conducting investigations and provide detailed disclosure of their intentions. When adverse employment decisions result from background check findings, candidates receive copies of their reports and summaries of their rights under federal law.
FCRA's adverse action procedures require employers to provide pre-adverse action notices that allow candidates to review and dispute concerning information before final decisions. This process gives individuals opportunities to correct errors, provide context for past incidents, or present evidence of changed circumstances that might influence hiring decisions.
FCRA Protection Timeline:
- Initial Disclosure: Clear notification of background check intent
- Consent Requirement: Written authorization before investigation begins
- Pre-Adverse Action: Notice and waiting period before negative decisions
- Final Adverse Action: Formal notification with dispute rights information
Arizona candidates should understand their rights to request copies of background reports used in employment decisions. Annual credit report reviews can help identify errors before they affect job opportunities, and prompt dispute resolution can prevent recurring problems in future employment screening.
Arizona State Protections
Arizona provides additional protections beyond federal requirements, particularly regarding arrest record usage and consent procedures. State law generally discourages employers from considering arrest records that didn't result in convictions when making hiring decisions. This protection helps ensure that individuals aren't unfairly penalized for accusations that weren't proven in court.
The state's consent requirements mandate clear disclosure of background check scope and candidate agreement before investigations begin. These requirements promote transparency and help ensure that candidates understand what information employers will review during the screening process. Proper consent procedures also protect employers from legal challenges related to unauthorized investigations.
Arizona's regulatory framework continues evolving to balance employer security needs with candidate privacy rights. Recent developments include enhanced data protection requirements and expanded access to background check information for individuals seeking to understand and correct their records.
Best Practices for Job Seekers
Successful navigation of Arizona data center background checks requires proactive preparation and strategic transparency. Candidates who understand the screening process and prepare accordingly often experience smoother hiring experiences and better employment outcomes. The key lies in controlling available information and presenting it in the most favorable context possible.
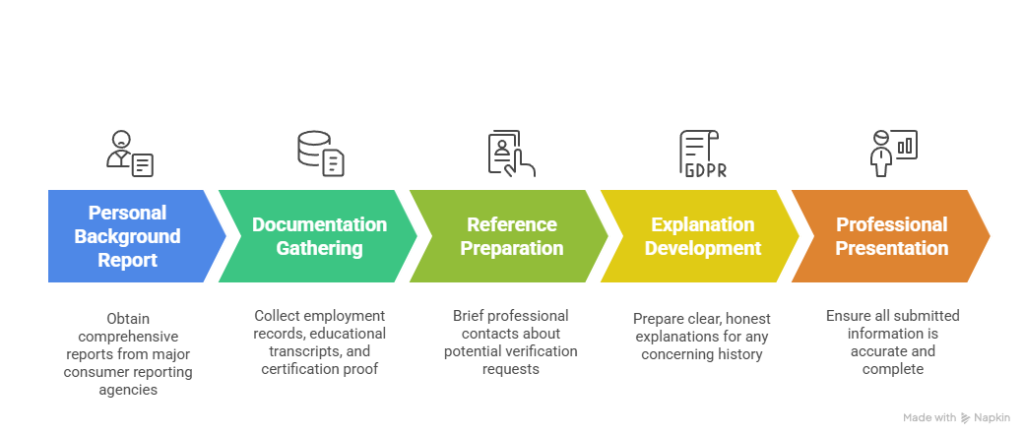
Essential Preparation Steps:
- Personal Background Report: Obtain comprehensive reports from major consumer reporting agencies
- Documentation Gathering: Collect employment records, educational transcripts, and certification proof
- Reference Preparation: Brief professional contacts about potential verification requests
- Explanation Development: Prepare clear, honest explanations for any concerning history
- Professional Presentation: Ensure all submitted information is accurate and complete
Transparency represents the most effective strategy for addressing potential background check concerns. Candidates who proactively discuss past issues and demonstrate personal growth often fare better than those who attempt to conceal information that will likely be discovered during investigations.
The digital age requires additional preparation regarding online presence and social media activity. Arizona data center candidates should review their digital footprints and address any content that might raise security concerns or professional questions during the screening process.
Employer Compliance Requirements
Arizona data center employers must navigate complex compliance requirements spanning federal and state regulations. FCRA compliance forms the foundation of legal background screening, requiring specific procedures for obtaining consent, conducting investigations, and handling adverse decisions. Violations can result in significant financial penalties and legal challenges that far exceed the costs of proper compliance.
Core Compliance Elements:
- Written Consent: Clear, standalone authorization documents
- Proper Disclosure: Comprehensive notification of screening scope
- Adverse Action Procedures: Structured process for negative hiring decisions
- Record Retention: Appropriate storage and disposal of screening documentation
- Ongoing Training: Staff education about legal requirements and best practices
State-level compliance adds layers of complexity, particularly regarding "ban the box" policies for public sector positions and consent requirements that exceed federal minimums. Employers must stay current with regulatory changes and adapt their procedures accordingly to maintain legal compliance.
Regular legal review of background screening procedures helps identify potential compliance gaps before they result in violations. Many employers benefit from partnerships with specialized background screening companies that maintain current knowledge of evolving legal requirements and industry best practices.
Cost Considerations and Budget Planning
Background screening costs vary significantly based on investigation scope, timeline requirements, and security clearance needs. Arizona data center employers should develop comprehensive budgets that account for both routine screening and enhanced investigations required for sensitive positions. Proper budget planning prevents cost overruns while ensuring adequate security screening coverage.
Cost Structure Analysis:
| Screening Type | Price Range | Timeline | Typical Use Cases |
| Basic Verification | $25-$50 | 3-7 days | Entry-level positions |
| Enhanced Screening | $100-$300 | 7-14 days | Technical roles |
| Security Clearance | $500-$15,000+ | 30-90+ days | Classified environments |
Volume screening agreements with background check providers can reduce per-check costs while ensuring consistent service quality. Many employers negotiate annual contracts that provide predictable pricing and priority processing for urgent hiring needs.
The investment in comprehensive background screening often generates positive returns through reduced employee turnover, improved security outcomes, and enhanced regulatory compliance. These benefits typically justify screening costs while supporting long-term organizational success.
Conclusion
Arizona data center background check requirements represent a complex intersection of federal security mandates, state privacy protections, and industry-specific screening needs. Success requires understanding multiple regulatory frameworks while implementing practical strategies that balance security concerns with fair employment practices. Both employers and job seekers benefit from proactive preparation, transparent communication, and ongoing awareness of evolving compliance requirements. As technology and regulations continue advancing, staying informed and adaptable will remain essential for navigating Arizona's data center employment landscape successfully.
Frequently Asked Questions
How far back do Arizona data center background checks typically look?
Arizona allows indefinite criminal history reporting under FCRA guidelines, meaning background checks can reveal convictions from any point in your history. However, most employers focus on the past 7-10 years for employment and education verification, while considering older criminal records based on their relevance to job responsibilities.
What is the difference between standard and enhanced background checks for Arizona data centers?
Standard checks cost $25-$50 and take 3-7 days, covering basic criminal history, identity verification, and employment confirmation. Enhanced checks for security clearance positions can cost up to $15,000+ and take 30-90 days, including FBI fingerprinting, financial assessments, and comprehensive federal investigations.
Does Arizona's "ban the box" law apply to private data center employers?
No, Arizona Executive Order 2017-07 only prohibits public sector employers from asking about criminal history on initial applications. Private data center companies can inquire about criminal records at any point in their hiring process, though many choose to delay these discussions until after conditional job offers.
What types of criminal history typically disqualify candidates from data center positions?
Common disqualifiers include violent crimes, financial fraud, cybercrime convictions, and recent drug-related offenses. However, employers must consider factors like time elapsed since conviction, evidence of rehabilitation, and job relevance when making decisions based on criminal history.
How do SRP and APS energy requirements affect data center background checks?
Both utilities impose additional screening requirements including NERC CIP compliance for grid-connected facilities. This includes enhanced financial background checks, cybersecurity assessments, and ongoing personnel revalidation beyond standard employment screening requirements.
Can I dispute errors found in my Arizona data center background check?
Yes, FCRA provides comprehensive dispute rights. If you find inaccuracies, contact the consumer reporting agency that prepared the report to initiate corrections. Employers must provide pre-adverse action notices that give you time to review and dispute concerning information before final hiring decisions.
What documentation should I prepare before applying for Arizona data center positions?
Gather employment records, educational transcripts, professional certifications, and any court documents related to criminal history. Prepare clear explanations for employment gaps or past issues, and ensure all contact information for references and former employers is current and accurate.
How long does it take to obtain security clearance for sensitive data center positions?
Federal security clearances typically require 30-90 days or longer, depending on investigation complexity and agency workloads. Factors like international travel, foreign contacts, or complex employment history can extend processing times significantly beyond standard expectations.
Additional Resources
- Arizona Department of Public Safety Background Check Information
https://www.azdps.gov/services/public/fingerprint - Fair Credit Reporting Act Compliance Guide
https://www.ftc.gov/business-guidance/resources/fair-credit-reporting-act - DHS CFATS Program Overview
https://www.cisa.gov/chemical-facility-anti-terrorism-standards - NERC Critical Infrastructure Protection Standards
https://www.nerc.com/pa/Stand/Pages/CIPStandards.aspx - Salt River Project Security Requirements
https://www.srpnet.com/business/doing-business/security-requirements - Arizona Public Service Cybersecurity Guidelines
https://www.aps.com/en/About/Our-Company/Cybersecurity
Still have questions?
Get in touch with our team today for a personalized demo and discover how our tailored volume pricing and packages can drive results for your business!
How useful was this page?*
Note: your comments are anonymous. We use them to improve the website. Do not include any personal details.
Visit our FCRA Compliance Tool or leave a message here if you need a response.
From the blog Explore the GCheck Content Hub

How Long Do Background Checks Take for Government Jobs? Timeline Expectations for 2026
6 Jan, 2026 • 20 min read
Driver Qualification File Requirements: Your Complete DOT Compliance Guide
6 Jan, 2026 • 18 min read
Healthcare Background Screening Costs: 2026 Budget Planning Guide for Medical Facilities
30 Dec, 2025 • 23 min readThe information provided in this article is for general informational and educational purposes only and should not be construed as legal advice or a substitute for consultation with qualified legal counsel. While we strive to ensure accuracy, employment screening laws and regulations—including but not limited to the Fair Credit Reporting Act (FCRA), Equal Employment Opportunity Commission (EEOC) guidelines, state and local ban-the-box laws, industry-specific requirements, and other applicable federal, state, and local statutes—are subject to frequent changes, varying interpretations, and jurisdiction-specific applications that may affect their implementation in your organization. Employers and screening decision-makers are solely responsible for ensuring their background check policies, procedures, and practices comply with all applicable laws and regulations relevant to their specific industry, location, and circumstances. We strongly recommend consulting with qualified employment law attorneys and compliance professionals before making hiring, tenant screening, or other decisions based on background check information.

