CMMC background check requirements represent a critical compliance component for defense contractors handling Controlled Unclassified Information (CUI). However, CMMC certification itself doesn't mandate specific personnel screening protocols. Instead, contractors must implement background investigations aligned with NIST SP 800-171 and DFARS 7012 standards based on their access levels and contract requirements. This guide translates DoD cybersecurity mandates into actionable screening protocols that satisfy federal contractor employee screening obligations while protecting contract eligibility and organizational security posture.
Key Takeaways
- CMMC certification doesn't explicitly require background checks, but NIST SP 800-171 control PS-3 mandates personnel screening commensurate with risk levels for individuals accessing CUI systems.
- Defense contractors must implement tiered screening protocols based on access levels, with minimum requirements including identity verification, employment history, and criminal records checks for CUI access.
- DFARS compliance background checks differ from traditional security clearances—most CMMC-regulated contractors need robust commercial screening rather than government-issued clearances unless specified by contract.
- Federal contractor employee screening programs must document screening criteria, investigation scope, and rescreening intervals in formal personnel security policies required for CMMC Level 2 compliance.
- Cybersecurity contractor vetting requirements extend beyond traditional background checks to include technical competency verification, insider threat indicators, and continuous evaluation programs.
- FCRA compliance remains mandatory for all employment-related background checks, requiring proper authorization, adverse action procedures, and disclosure protocols even within DoD contractor security clearance background check frameworks.
- Implementation timelines should account for 2-6 week screening completion periods, with expedited processes available for critical positions requiring immediate CUI access.
- Non-compliance with CMMC compliance personnel screening requirements can result in contract ineligibility, with DoD implementing full CMMC enforcement across the Defense Industrial Base starting in 2025.
Understanding CMMC Background Check Requirements
The Cybersecurity Maturity Model Certification (CMMC) framework establishes cybersecurity standards for defense contractors. This creates confusion about specific personnel screening obligations. While CMMC doesn't explicitly mandate "background checks" as a standalone requirement, the underlying NIST SP 800-171 controls that form CMMC's foundation include personnel security requirements. These controls effectively necessitate background investigations. Understanding this distinction helps HR professionals implement compliant screening programs without over-investing in unnecessary security measures.
CMMC 2.0, implemented throughout 2024 and enforced in 2025, consolidates the original five-level model into three levels: Foundational, Advanced, and Expert. Level 2 (Advanced) applies to most contractors handling CUI and incorporates all 110 NIST SP 800-171 security requirements. This includes the PS (Personnel Security) family of controls. These controls establish the legal basis for DoD contractor security clearance background check requirements. However, they specify outcomes rather than prescriptive screening methodologies.
The enforcement landscape shifted significantly in 2024, with CMMC language appearing in new DoD contracts. Existing contracts were modified to include CMMC compliance clauses. Defense contractors face contract ineligibility if they cannot demonstrate CMMC certification at required levels. This makes personnel security screening an organizational imperative rather than optional enhancement. This compliance obligation extends throughout the supply chain, affecting subcontractors and service providers with CUI access regardless of contract size.
NIST SP 800-171 Personnel Security Controls
NIST SP 800-171 establishes four personnel security controls under the PS family, with PS-3 (Personnel Screening) serving as the primary driver for background check requirements. This control requires organizations to screen individuals before authorizing access to organizational systems containing CUI, with screening criteria commensurate with risk level, information classification, and applicable legal requirements. The control deliberately avoids prescriptive requirements, allowing organizations to tailor screening depth based on specific operational contexts while maintaining CMMC compliance.
The PS family encompasses interconnected controls governing personnel security throughout the employment lifecycle:
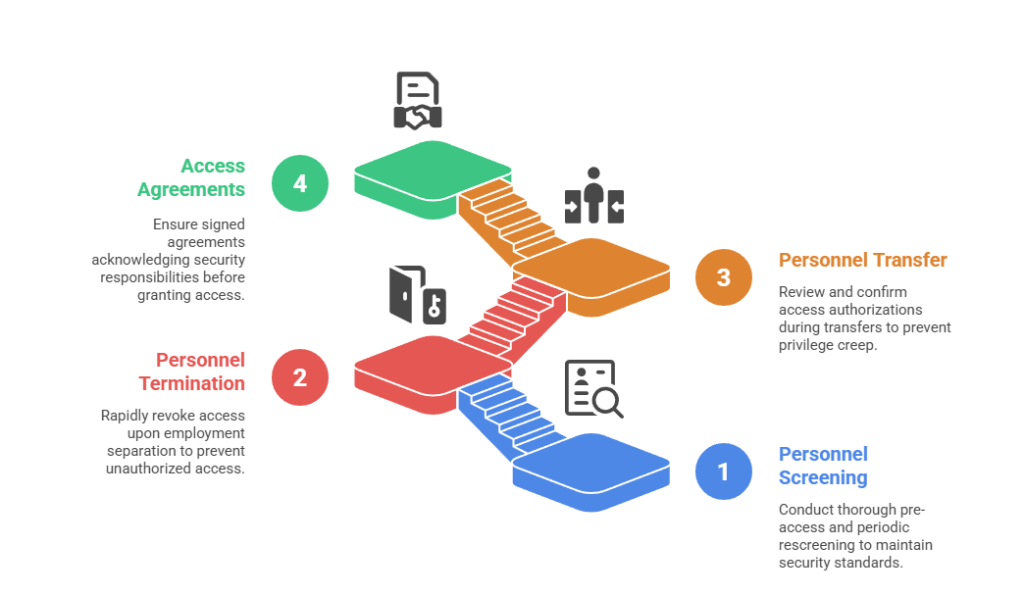
- PS-3 Personnel Screening: Mandates pre-access screening and periodic rescreening based on organizational policy, with formal screening criteria documented in personnel security policies required for CMMC assessment.
- PS-4 Personnel Termination: Requires rapid access revocation upon employment separation, including system access disablement, exit interviews, credential retrieval, and organizational property return within hours of termination notification.
- PS-5 Personnel Transfer: Mandates review and confirmation of logical and physical access authorizations when personnel transfer to different positions, preventing privilege creep while ensuring appropriate access for new responsibilities.
- PS-6 Access Agreements: Requires signed access agreements acknowledging security responsibilities before granting system access, with periodic renewals confirming ongoing compliance obligations.
These controls work together to create comprehensive personnel security programs addressing hiring, ongoing employment, internal transfers, and separation. Organizations must implement all four controls to achieve CMMC Level 2 certification while demonstrating risk-based decision making throughout the personnel security lifecycle.
PS-3 Personnel Screening Requirements
Rescreening intervals vary based on position sensitivity and organizational risk tolerance. Most contractors implement 3-5 year cycles for standard CUI access. More frequent reviews apply for privileged system administrators. Organizations must also establish trigger-based rescreening for significant life events, security incidents, or behavioral indicators suggesting insider threat risks. These protocols demonstrate the continuous evaluation approach assessors expect during CMMC Level 2 certification.
PS-4 Personnel Termination Procedures
PS-4 addresses access revocation upon employment termination. Organizations must disable system access, conduct exit interviews, retrieve authentication credentials, and ensure returning organizational property. While not directly a background check requirement, PS-4 connects to screening programs through comprehensive personnel security lifecycle management. Exit interviews should document final access dates, confirm returned credentials, and reinforce confidentiality obligations regarding CUI exposure.
Termination procedures must execute rapidly—typically within hours of separation notification—to minimize unauthorized access windows. Automated workflows linking HR systems to access management platforms ensure consistent execution, particularly for large organizations with multiple facilities. Documentation should capture termination dates, access revocation confirmation, credential recovery, and exit interview completion. This creates audit trails demonstrating PS-4 compliance.
PS-5 Personnel Transfer Requirements
PS-5 mandates review and confirmation of logical and physical access authorizations when personnel transfer to different positions within the organization. This control recognizes that internal transfers may change CUI access requirements. This necessitates screening updates or access modifications. Organizations must establish transfer notification workflows ensuring security teams review access rights before personnel assume new responsibilities.
Transfer reviews should evaluate whether new positions require additional screening. For example, upgrading from basic CUI access to system administrator privileges may require enhanced background investigations. Documentation must capture transfer dates, access reviews conducted, screening updates completed, and approval authorizations. This systematic approach prevents privilege creep while ensuring personnel maintain appropriate access for current responsibilities.
Tiered Screening Protocols for Defense Contractors
Defense contractors should implement tiered screening protocols matching investigation depth to access levels and position sensitivity. This risk-based approach optimizes resource allocation while ensuring compliance with CMMC compliance personnel screening requirements. Three-tier frameworks effectively address most organizational needs, with customization available for unique operational contexts.
| Access Tier | Screening Components | Typical Positions |
| Basic CUI Access | Identity verification, 7-year criminal history, employment verification (5 years), education confirmation, SSN trace | Administrative staff, general users with limited CUI exposure |
| Privileged CUI Access | All Basic components plus: credit history review, professional reference interviews (3-5), drug screening, motor vehicle records | System administrators, cybersecurity personnel, contracts managers |
| Critical Infrastructure | All Privileged components plus: enhanced criminal history (10+ years), federal database checks, continuous monitoring enrollment | CUI system owners, security officers, senior IT leadership |
This framework provides clear guidance for determining appropriate screening depth. Each tier builds upon the previous level, adding investigative components proportional to access sensitivity and insider threat potential.
Basic Tier Screening Components
Basic tier screenings establish fundamental trustworthiness for personnel with routine CUI access. They focus on identity confirmation and disqualifying criminal histories. Investigations typically complete within 5-10 business days using commercial background screening providers. This makes this tier appropriate for high-volume hiring scenarios. Criminal history searches should cover all jurisdictions where candidates resided during the lookback period, typically seven years per FCRA guidance.
Privileged Tier Screening Components
Privileged tier screenings add financial responsibility evaluation and enhanced reference verification for positions with elevated insider threat potential. System administrators and cybersecurity personnel require deeper investigation given their technical capabilities to exfiltrate, modify, or destroy CUI. Credit history reviews identify financial distress that might motivate malicious activity. Meanwhile, professional references verify technical competency claims and assess behavioral reliability.
Critical Infrastructure Tier Screening
Critical infrastructure tier screenings approach security clearance rigor for personnel with broad system access or security program responsibilities. These investigations may include federal database checks (FBI Criminal Justice Information Services, GSA System for Award Management). They also involve continuous monitoring enrollment through services like NIST's Continuous Diagnostics and Mitigation program. In some cases, periodic polygraph examinations apply for highest-sensitivity positions. Timeline expectations extend to 4-6 weeks given investigation complexity.
Position Risk Assessment Methodology
Organizations must establish systematic position risk assessment methodologies determining appropriate screening tiers for each role. Assessment criteria should evaluate CUI access scope, system privilege levels, physical access to secure areas, and potential damage from insider actions. Documented risk assessments demonstrate the commensurate screening rationale CMMC assessors expect during PS-3 evaluation.
Risk assessment workflows typically begin during position creation or modification. Security teams evaluate proposed responsibilities against established criteria. High-risk factors include administrative credentials, database access, network infrastructure management, and unmonitored CUI system access. Organizations should document assessment results, tier assignments, and approval authorizations in personnel security files, updating assessments when position responsibilities change materially.
DFARS Compliance Background Checks vs. Security Clearances
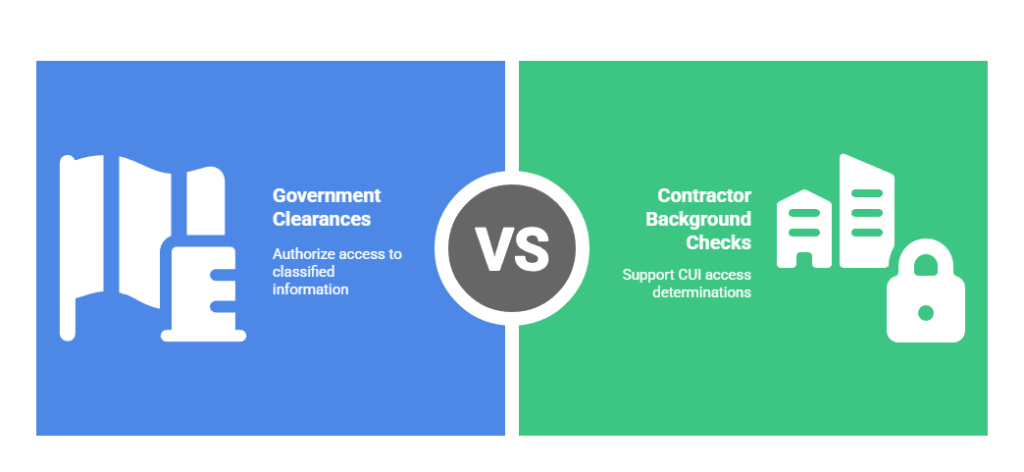
Federal contractor employee screening under DFARS differs fundamentally from government security clearances, though terminology confusion persists across the defense industrial base. Security clearances (Confidential, Secret, Top Secret) are government-issued determinations authorizing access to classified national security information processed through the Defense Counterintelligence and Security Agency (DCSA). In contrast, DFARS compliance background checks are contractor-administered investigations supporting CUI access determinations under NIST SP 800-171, not classified information access.
Key distinctions between these screening types include:
- Authority and administration: Security clearances are government-issued through DCSA investigations, while DFARS background checks are contractor-administered using commercial screening providers or internal capabilities.
- Information type protected: Clearances authorize access to classified national security information, while DFARS screening supports CUI access determinations under NIST SP 800-171.
- Investigation scope: Government clearances involve extensive federal database checks, subject interviews, and reference investigations by government investigators (Tier 3 for Secret, Tier 5 for Top Secret), while contractor screening depth varies based on organizational risk assessment and position sensitivity.
- Timeline expectations: Secret clearances typically process within 3-6 months and Top Secret clearances may require 12-18 months, while commercial background checks complete within 5-10 business days for standard investigations.
- Cost responsibility: Government absorbs clearance investigation costs, while contractors fund commercial background screening programs from operational budgets.
- Flexibility and control: Contractors maintain autonomy over DFARS screening criteria, vendor selection, and investigation scope within NIST parameters, while clearance requirements follow standardized government protocols without contractor discretion.
Most CMMC-regulated contractors handle CUI rather than classified information, requiring robust commercial background screening rather than security clearances unless contracts explicitly specify cleared personnel through DD Form 254 documentation. This autonomy enables cost optimization and timeline management while maintaining compliance with cybersecurity contractor vetting requirements.
When Security Clearances Are Required
Security clearances become mandatory when contracts involve classified information access, work on classified programs, or access to government secure facilities. Contract documentation explicitly identifies clearance requirements through DD Form 254 (DoD Contract Security Classification Specification). This outlines security classification levels, visit requirements, and personnel security mandates. Contractors cannot substitute commercial background checks for clearance requirements when contracts specify cleared personnel.
The clearance process begins with contractor sponsorship, submitting SF-86 (Questionnaire for National Security Positions) through DCSA's electronic system. Investigation timelines vary significantly—Secret clearances typically process within 3-6 months. Top Secret clearances may require 12-18 months given investigation complexity. Contractors should initiate clearance processes early during contract pursuit to avoid personnel shortages delaying contract execution.
Integrating Clearance and CMMC Screening
Organizations with both classified and CUI programs must integrate security clearance and CMMC screening requirements into unified personnel security programs. Cleared personnel generally exceed CMMC screening requirements. However, contractors should document how clearance investigations satisfy PS-3 controls during CMMC assessment. Security clearances don't eliminate CMMC compliance obligations—organizations must still implement remaining NIST SP 800-171 controls addressing access management, incident response, and system security.
Documentation should map clearance investigation components to PS-3 screening criteria, demonstrating equivalent or superior rigor. Clearance reciprocity between cleared personnel enables efficient onboarding when workers transfer between classified and CUI programs. Personnel security policies should address screening requirements for uncleared personnel on mixed programs. This ensures all CUI access receives appropriate screening regardless of clearance status.
Implementing Compliant Screening Programs
Effective implementation requires documented policies, qualified screening vendors, compliant processes, and auditable records supporting CMMC assessment. Organizations should approach personnel security program development systematically. This means establishing foundational policy frameworks before executing screening operations. This structured approach prevents compliance gaps while building sustainable programs scalable across organizational growth.
Personnel security policies must define screening criteria for each access tier, investigation scope and methodology, adjudication standards, rescreening intervals, and continuous evaluation triggers. Policies should integrate with broader security documentation required for CMMC. This includes System Security Plans (SSPs) and Plans of Action and Milestones (POA&Ms). CMMC assessors evaluate policy completeness, implementation evidence, and control effectiveness during certification audits. This requires organizations to demonstrate operational screening programs rather than theoretical frameworks.
Vendor Selection and FCRA Compliance
Selecting qualified background screening vendors represents a critical implementation decision affecting compliance, cost, and operational efficiency. Vendors must demonstrate FCRA compliance capabilities including proper disclosure delivery, authorization collection, adverse action notification, and dispute resolution procedures. Defense contractors remain legally liable for FCRA violations even when outsourcing screening execution, making vendor due diligence essential.
Qualified vendors should offer the following capabilities:
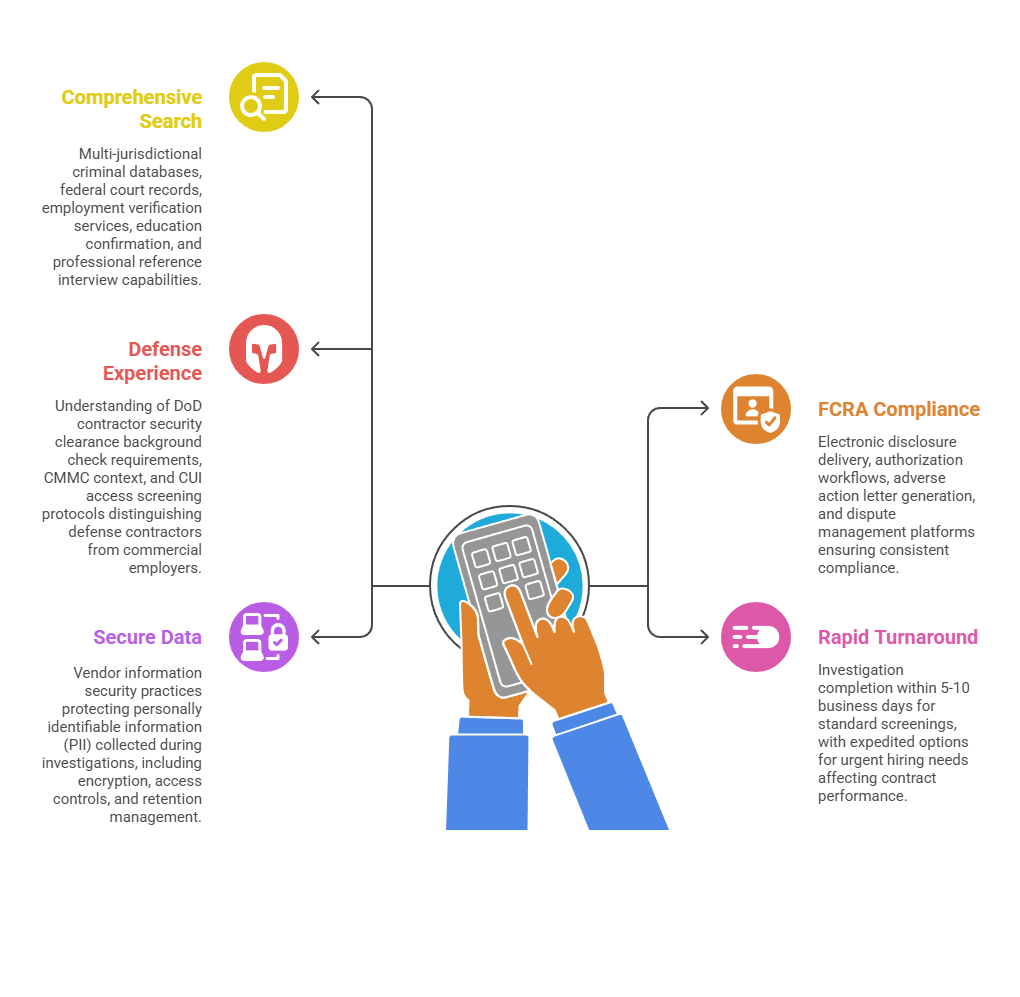
- Comprehensive search capabilities: Multi-jurisdictional criminal databases, federal court records, employment verification services, education confirmation, and professional reference interview capabilities.
- FCRA compliance automation: Electronic disclosure delivery, authorization workflows, adverse action letter generation, and dispute management platforms ensuring consistent compliance.
- Defense industry experience: Understanding of DoD contractor security clearance background check requirements, CMMC context, and CUI access screening protocols distinguishing defense contractors from commercial employers.
- Rapid turnaround times: Investigation completion within 5-10 business days for standard screenings, with expedited options for urgent hiring needs affecting contract performance.
- Secure data handling: Vendor information security practices protecting personally identifiable information (PII) collected during investigations, including encryption, access controls, and retention management.
Vendor evaluation should include reference checks from other defense contractors, sample report review, pricing transparency analysis, and customer support assessment. Contract negotiations should address service level agreements, investigation quality guarantees, and liability allocations for compliance failures.
FCRA Compliance Requirements
The Fair Credit Reporting Act establishes legal requirements for employment-related background checks. These apply fully to defense contractor screening programs regardless of CMMC obligations. Compliance requires specific procedural steps before, during, and after background investigations. Technical violations create legal exposure through private rights of action. HR professionals must integrate FCRA requirements into CMMC screening protocols, recognizing that cybersecurity compliance doesn't supersede employment law obligations.
Pre-screening requirements include providing standalone disclosure documents notifying candidates that background checks will be conducted. These explain the nature and scope of investigations. Disclosures cannot be embedded within employment applications or other documents—FCRA mandates standalone formats ensuring candidate awareness. Organizations must obtain written authorization before initiating investigations, using clear language without liability waivers or other non-disclosure content.
Adverse action procedures apply when screening results inform negative employment decisions. Organizations must provide pre-adverse action notices including investigation reports and FCRA summary of rights. This allows candidates reasonable time (typically 5 business days) to dispute inaccuracies before finalizing employment decisions. Final adverse action notices must identify the screening vendor, explain dispute rights, and clarify that vendors don't make employment decisions. These procedural protections prevent unfair denials based on inaccurate information while creating documentation demonstrating FCRA compliance.
Documentation and Record Retention
Comprehensive documentation supports both CMMC assessment and legal compliance. This requires systematic record retention addressing personnel security activities. Organizations must maintain screening authorizations, investigation reports, adjudication decisions, and rescreening schedules in secure, auditable formats. Documentation systems should restrict access to personnel security personnel and authorized auditors. This protects sensitive PII while enabling compliance verification.
Record retention periods must satisfy multiple regulatory frameworks. FCRA requires maintaining background check records for positions accepted and adverse action documentation for rejected candidates (typically 2-5 years depending on state law). NIST SP 800-171 doesn't specify retention periods, though CMMC assessment requires demonstrating historical screening compliance through maintained records. Federal contractors should generally retain personnel security records for 7 years post-separation, aligning with general government contract record retention requirements under FAR 4.705.
Continuous Evaluation and Monitoring
NIST SP 800-171 emphasizes ongoing personnel security through rescreening and continuous evaluation programs. These detect post-hiring risk indicators. Traditional periodic rescreening (every 3-5 years) provides point-in-time risk assessments. Meanwhile, continuous monitoring delivers near-real-time notification of criminal activity, financial distress, or other concerning events. Leading defense contractors increasingly adopt continuous monitoring technologies supplementing periodic investigations, particularly for privileged access positions.
Continuous monitoring services query criminal databases, credit reporting systems, and public records repositories regularly (typically daily or weekly). They alert organizations when enrolled personnel experience triggering events. Common triggers include arrests, criminal convictions, significant credit delinquencies, bankruptcies, and inclusion on government exclusion lists. Organizations establish trigger response protocols determining when events warrant access suspension, additional investigation, or employment action.
Trigger Event Response Protocols
Documented response protocols ensure consistent, appropriate reactions to continuous monitoring alerts. Not all triggers warrant immediate access revocation—organizations must balance security risk against employee rights and operational continuity. Response protocols should categorize triggers by severity, establishing timelines for investigation, interim access decisions, and final determinations.
High-severity triggers include violent crime arrests, espionage-related charges, and terrorist watch list inclusion, which typically mandate immediate access suspension pending investigation. Moderate triggers encompass property crime arrests, financial delinquencies, and civil judgments that may warrant enhanced monitoring without immediate access restriction. Low-severity events cover traffic violations and minor civil disputes that generally require documentation without access impact unless patterns emerge.
Investigation workflows should include notification to personnel security staff, preliminary fact-gathering, employee interview when appropriate, and documented risk assessment. Legal counsel should review response protocols ensuring compliance with employment law, avoiding discriminatory practices or premature adverse actions violating due process obligations.
Special Considerations for Remote Workforce

The defense contractor remote workforce expanded significantly during 2020-2024. This created personnel security challenges for organizations with distributed CUI access. Remote workers accessing CUI systems from home networks require identical screening rigor as on-site personnel. However, organizations must implement additional security controls addressing remote access risks. Personnel security programs should address remote worker screening, home office security requirements, and continuous monitoring for distributed workforce.
Remote positions may warrant enhanced screening given reduced physical security controls and limited management visibility. Organizations should evaluate financial responsibility more heavily for remote workers. This recognizes that financial pressures combined with unsupervised CUI access increase insider threat risk. Technical competency verification becomes critical for remote IT personnel. This ensures individuals possess skills for secure remote system administration without on-site supervision.
Home office security requirements should supplement personnel screening. These address physical security, network security, and family member access prevention. Organizations may require home office inspections verifying adequate security controls before authorizing remote CUI access. Written agreements should establish remote worker security obligations, including dedicated workspace requirements, network security standards, and prohibition on unauthorized personnel accessing government systems.
Common Implementation Challenges and Solutions
Defense contractors encounter predictable challenges implementing CMMC compliance personnel screening. These range from budget constraints to timeline pressures affecting hiring operations. Proactive challenge identification and solution development prevents compliance gaps while maintaining operational efficiency. Organizations should anticipate common obstacles during program design, building mitigation strategies into foundational policies and procedures.
Budget Constraints for Comprehensive Screening
Background screening costs accumulate rapidly for organizations with significant hiring volumes, creating budget pressures that tempt shortcuts compromising compliance. Commercial screening costs range from $25-75 per candidate for basic checks to $200-400 for comprehensive investigations including credit reports and professional references. Organizations hiring dozens or hundreds of personnel annually face five-figure screening expenses before considering program administration overhead.
Budget solutions include the following approaches:
- Tiered screening approaches: Implementing risk-based investigation depth prevents over-screening low-risk positions while concentrating resources on privileged access roles.
- Volume pricing negotiation: Establishing master service agreements with screening vendors delivers per-unit cost reductions through volume commitments.
- Technology automation: Investing in applicant tracking systems with integrated screening workflows reduces administrative labor costs managing manual processes.
- Periodic rescreening optimization: Extending rescreening intervals for lowest-risk positions (from 3 to 5 years) reduces recurring investigation costs without material security degradation.
Organizations should view screening costs as contract enablement expenses rather than optional overhead. Contract ineligibility from CMMC non-compliance creates revenue losses vastly exceeding screening investment, making personnel security programs essential business infrastructure.
Balancing Speed and Thoroughness
Defense contractors face constant tension between hiring speed and investigation thoroughness. This becomes especially acute when contract awards create immediate staffing needs. Comprehensive background investigations require 2-4 weeks minimum, potentially delaying critical position fills. Organizations pressure screening vendors for rapid turnaround, sometimes accepting incomplete investigations risking compliance violations and security gaps.
Solutions require process optimization and realistic timeline expectations. Organizations should initiate screening immediately upon conditional offer acceptance rather than waiting for start date proximity. Expedited screening options available from premium vendors complete basic investigations within 48-72 hours using electronic databases and rapid verification services. However, costs increase 50-100% over standard timelines. Provisional access protocols enable personnel to begin non-CUI work while investigations complete, maintaining productivity without security compromise.
Hiring managers require education about investigation timelines. They must build screening duration into hiring plans rather than expecting instant completion. Organizations should establish target hiring timelines incorporating background check completion, typically 3-4 weeks from offer acceptance to start date. This realistic scheduling prevents shortcuts compromising investigation quality or compliance requirements.
Conclusion
CMMC background check requirements reflect the Defense Department's recognition that personnel security forms a critical foundation for cybersecurity program effectiveness. While CMMC doesn't prescribe specific screening methodologies, the underlying NIST SP 800-171 controls establish clear expectations for risk-based personnel investigations, documented policies, and continuous evaluation programs. Defense contractors implementing systematic screening programs aligned with PS-3 requirements simultaneously address CMMC compliance obligations and build robust insider threat mitigation capabilities protecting organizational security. As DoD implements full CMMC enforcement throughout 2025, personnel security programs will face increasing scrutiny during certification assessments, making comprehensive screening protocols an immediate priority for contractors across the defense industrial base.
Frequently Asked Questions
Does CMMC require security clearances for all defense contractors?
No, CMMC does not require security clearances for all defense contractors. CMMC certification focuses on cybersecurity controls protecting Controlled Unclassified Information (CUI), which differs from classified national security information requiring security clearances. Contractors only need security clearances when contracts explicitly involve classified information access, specified through DD Form 254 in contract documentation. Most CMMC-regulated contractors handle CUI exclusively and satisfy personnel security requirements through commercial background screening.
What background checks are required for CMMC Level 2 compliance?
CMMC Level 2 requires personnel screening commensurate with risk levels as specified in NIST SP 800-171 control PS-3, but doesn't mandate specific background check components. Organizations must establish screening criteria appropriate for their operational context, typically including identity verification, criminal history checks, employment verification, and education confirmation for basic CUI access. Privileged positions like system administrators generally require enhanced screening including credit history review, professional references, and drug testing. The key compliance factor is documented screening policies, consistent implementation, and rescreening protocols.
How often must defense contractors rescreen employees?
NIST SP 800-171 requires rescreening according to organizational policy or when circumstances warrant additional investigation, without specifying mandatory intervals. Most defense contractors implement 3-5 year rescreening cycles for personnel with CUI access, with more frequent reviews for system administrators and personnel with privileged access. Organizations should document rescreening intervals in personnel security policies based on position sensitivity and risk assessment. Trigger-based rescreening should occur for significant life events, security incidents, or behavioral indicators suggesting potential insider threats.
Can contractors use different screening criteria for different positions?
Yes, risk-based screening approaches using different criteria for different positions align with NIST SP 800-171's requirement for screening "commensurate with risk." Organizations should implement tiered screening protocols matching investigation depth to access levels and position sensitivity. Administrative staff with limited CUI exposure may require basic screening, while system administrators need enhanced investigations including credit history and professional references. Organizations must document the position risk assessment methodology determining appropriate screening tiers.
Are FCRA requirements waived for defense contractor security screening?
No, FCRA requirements apply fully to defense contractor background screening regardless of CMMC or security clearance context. The Fair Credit Reporting Act governs all employment-related background checks, requiring standalone disclosure documents, written authorization, and adverse action procedures when screening results inform negative employment decisions. Defense contractors must comply with both FCRA employment law requirements and NIST SP 800-171 security controls simultaneously. Government security clearance investigations conducted by DCSA operate under different authorities, but contractor-administered CMMC screening must follow standard FCRA protocols.
What happens if an employee fails a background check after starting work?
When current employees fail background checks—whether initial investigations delayed during expedited hiring or periodic rescreening—organizations must immediately suspend CUI access pending investigation and decision. Documented adverse action protocols should guide the process, including employee notification of concerning findings, opportunity to dispute inaccuracies, and review by personnel security officials. Employment termination isn't automatically required; organizations may reassign employees to non-CUI positions if business needs allow. FCRA adverse action procedures apply, requiring specific notification documents and dispute opportunities before final employment decisions.
How do continuous monitoring programs satisfy rescreening requirements?
Continuous monitoring programs supplement rather than replace periodic rescreening requirements under NIST SP 800-171. These services provide ongoing alerts about criminal activity, financial distress, and other triggering events between formal rescreening investigations, enhancing overall personnel security posture. Organizations implementing continuous monitoring may justify extended rescreening intervals (5 years vs. 3 years) given enhanced visibility into personnel risk indicators. CMMC assessors generally view continuous monitoring favorably as evidence of mature personnel security programs.
Can small defense contractors afford compliant background screening programs?
Yes, small defense contractors can implement compliant screening programs through risk-based approaches, technology leverage, and appropriate vendor partnerships. Basic commercial background checks cost $25-75 per candidate, manageable even for small organizations with limited hiring volumes. Many screening vendors offer small business pricing, electronic workflow platforms, and compliance support specifically designed for resource-constrained organizations. Small contractors should view screening costs as essential contract enablement expenses—non-compliance creates contract ineligibility threatening business viability.
Additional Resources
- NIST Special Publication 800-171 Revision 2: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
https://csrc.nist.gov/publications/detail/sp/800-171/rev-2/final - Department of Defense CMMC Program Overview and Latest Updates
https://www.acq.osd.mil/cmmc/ - Fair Credit Reporting Act Compliance Guide for Employment Screening
https://www.ftc.gov/business-guidance/resources/using-consumer-reports-what-employers-need-know - Defense Counterintelligence and Security Agency Personnel Security Programs
https://www.dcsa.mil/is/personnel-security/ - DFARS 252.204-7012 Safeguarding Covered Defense Information and Cyber Incident Reporting
https://www.acquisition.gov/dfars/252.204-7012-safeguarding-covered-defense-information-and-cyber-incident-reporting
Still have questions?
Get in touch with our team today for a personalized demo and discover how our tailored volume pricing and packages can drive results for your business!
How useful was this page?*
Note: your comments are anonymous. We use them to improve the website. Do not include any personal details.
Visit our FCRA Compliance Tool or leave a message here if you need a response.
From the blog Explore the GCheck Content Hub

DOT Physical Requirements for Drivers: 2026 Compliance Guide
9 Jan, 2026 • 17 min read
Healthcare Employee Background Check: What Employers Need to Know in 2026
9 Jan, 2026 • 19 min read
How Long Do Background Checks Take for Government Jobs? Timeline Expectations for 2026
6 Jan, 2026 • 20 min readThe information provided in this article is for general informational and educational purposes only and should not be construed as legal advice or a substitute for consultation with qualified legal counsel. While we strive to ensure accuracy, employment screening laws and regulations—including but not limited to the Fair Credit Reporting Act (FCRA), Equal Employment Opportunity Commission (EEOC) guidelines, state and local ban-the-box laws, industry-specific requirements, and other applicable federal, state, and local statutes—are subject to frequent changes, varying interpretations, and jurisdiction-specific applications that may affect their implementation in your organization. Employers and screening decision-makers are solely responsible for ensuring their background check policies, procedures, and practices comply with all applicable laws and regulations relevant to their specific industry, location, and circumstances. We strongly recommend consulting with qualified employment law attorneys and compliance professionals before making hiring, tenant screening, or other decisions based on background check information.

